HawkEye RAT- Posing as HSBC Notification
Blog
Thought Leadership
HawkEye RAT- Posing as HSBC Notification
Troy Gill

A new malware campaign is launching attacks on thousands of targets across the web. The malware laden emails pose as payment notification from HSBC bank. The messages direct the recipient to an attachment which attempts to appear to be a PDF. However, this is actually an archive(GZ) which contains an exe.
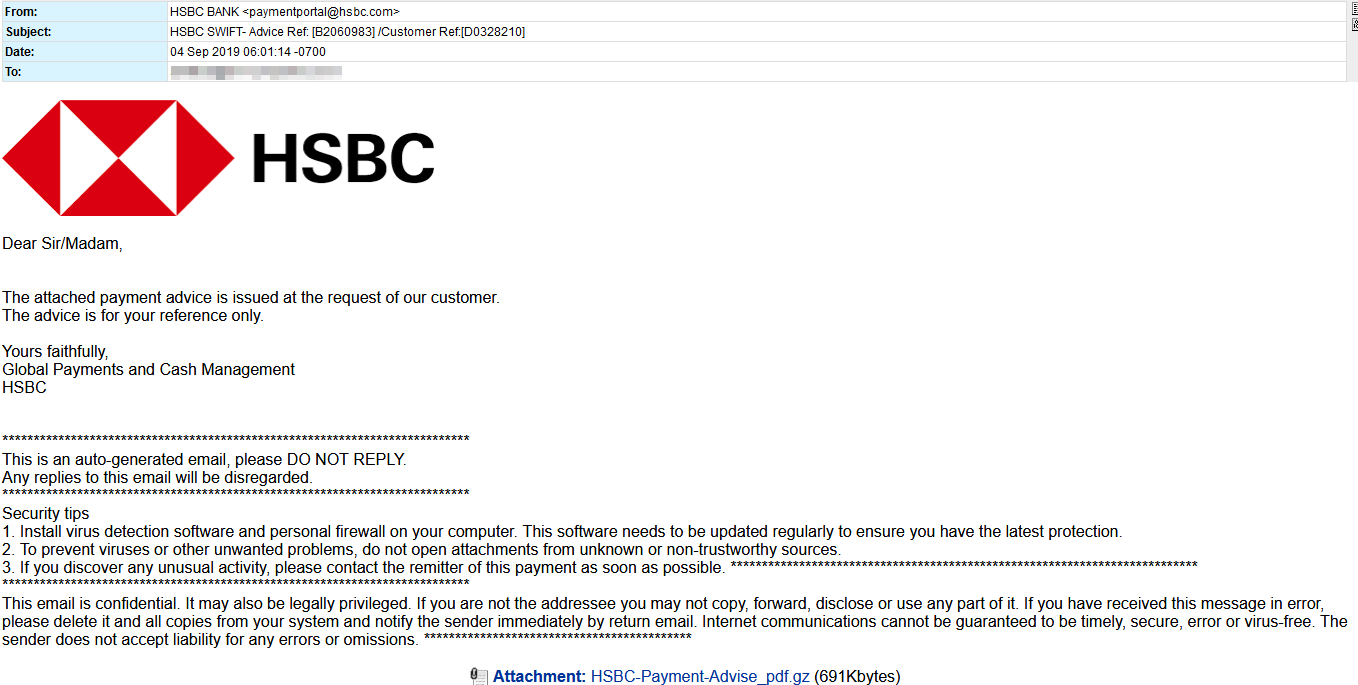
The malware being leveraged in this attack is none other than the HawkEye Reborn v9 RAT. HawkEye has been around for many years, with this latest version emerging in underground forums earlier this year. It is marketed as an “Advanced Monitoring Solution” complete with terms of service that prohibit its use on systems without permission. However, given the level of obfuscation and evasion (among other things) that is clearly built into the software, this is no doubt an attempt to shield its creators from culpability.
We observed this RAT attempting to evade analysis with VM awareness and multiple sandbox evasion routines and anti-debugging. During analysis we observed many of the functionalities that HawkEye is known for. Including harvesting browser history and passwords, stealing Instant messenger account info and passwords, harvesting mail credentials, creating an object for logging keystrokes and reading data from the clipboard.
So far this year we have seen an increase in RAT distribution. Of course, attackers will maximize returns on any and all data they are able to glean from each of their targets. Another possible eventuality is that the malware operators will use these infections to perform wide ranging reconnaissance on a targets network in order to launch and crippling ransomware attack that maximizes the potential a ransom will be paid.
IOCs observed:
https://a.pomf.cat/
JNZbzLtw.exe
