Bank of America Themed Emails Attempting to Spread Trickbot
Blog
Thought Leadership
Bank of America Themed Emails Attempting to Spread Trickbot
Troy Gill

On Jan 31, we noticed a large malware push posing as Bank of America that attempted to dupe users into opening an attachment. Opening the attachment would launch an infection chain that ultimately would lead to malware infection.
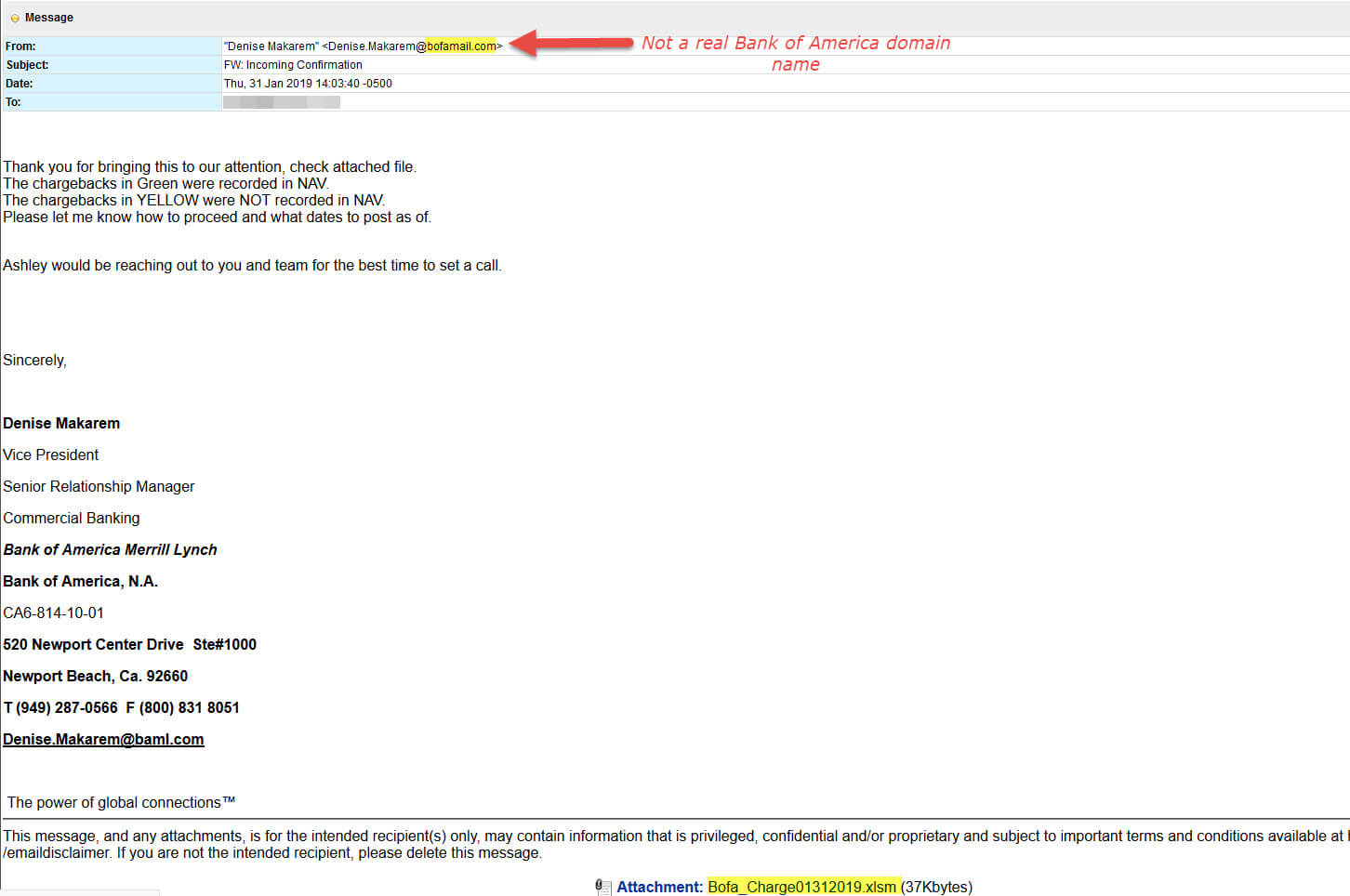
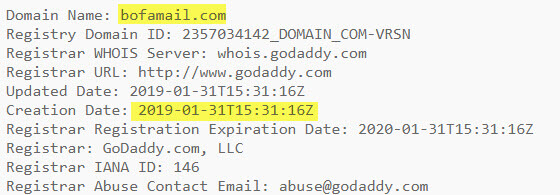
A little after 1 p.m. CST, a large email blast originating from the Netherlands began hitting our filters. The messages appeared to come from Bank of America, but as you can see from the examples below, the sending domain - bofamail[[dot]]com is not an official Bank of America domain - in fact, it was just registered Jan. 31 to an address in Amsterdam.
The .xlsm attachment in the message contains an OLE object that launches a loader that matches indicators for the Trickbot banking Trojan. We have written about this malware extensively over the past few years as it has remained quite active since its inception. Trickbot has received consistent upgrades over its life cycle. Among its many capabilities is the ability to leverage a worm component to spread laterally throughout the network.
To make matters worse, it was updated with modules to target cryptocurrency wallets such as Coinbase. However, its primary functionality is to commit financial theft. It contains routines to disable Windows Defender and other AV, evade sandboxing, code-injection, keylogging, contact scraping and startup persistence. It has also been observed dropping a Ransomware component as a final stage. In a nutshell it has fast become a veritable "Swiss Army knife of malware" and all around bad news.
In most of our run-ins of the past with this malware, it has been primarily targeting Western European businesses/entities/users. They generally do so by posing as an European banking institution. But today's campaign is much more U.S.-centric than we are used to seeing. Specifically, the BofA theme and majority US based targets. This could signal a shift or expansion in this criminal operation.
Just as fast as the malware campaign ramped up, it also ended abruptly having run its course in less than 2 hours. During that time, we quarantined more the 161,000 of these messages. It is not clear at this time whether or not the attackers were able to obtain a list of actual BofA customers or if if they were just playing the numbers. Though many of the businesses being targeted in this campaign do, in fact, have some sort of data exposed on the Dark Web.
All of our Advanced Email Security customers are fully protected from this threat.
******UPDATE******
We have recently observed Trickbot targeting the following Banks: