The Ongoing Emotet Campaigns
Blog
Thought Leadership
The Ongoing Emotet Campaigns
Bear Huddleston

Security specialists at AppRiver have been combating the nonstop and ever-changing Emotet campaigns.
The more you know and understand about Emotet campaigns, the better chance you'll have at staying protected. Knowledge of threats, coupled with best practices of safeguarding your information online is just as crucial as any solutions in place.
WHAT IS EMOTET?Emotet is a custom banking Trojan that relies on heavy obfuscation and evasion techniques to go undetected while committing financial theft. The Trojan spreads itself throughout the network by making use of its spreader module, brute forcing attacks within the network.
The main method Emotet uses to reach its target is malspam - emails containing malicious attachments or links. These emails often use branding familiar to the recipient, commonly spoofing someone in the same company or a known institution; similar to phishing campaigns.
Below are several examples of Emotet campaigns AppRiver's email security filters have intercepted. Here are some red flags for awareness.
Keep in mind that all URLs/hyperlinks directed to Emotet Trojan downloader; and recipient's email/signatures were blurred for privacy.
Example 1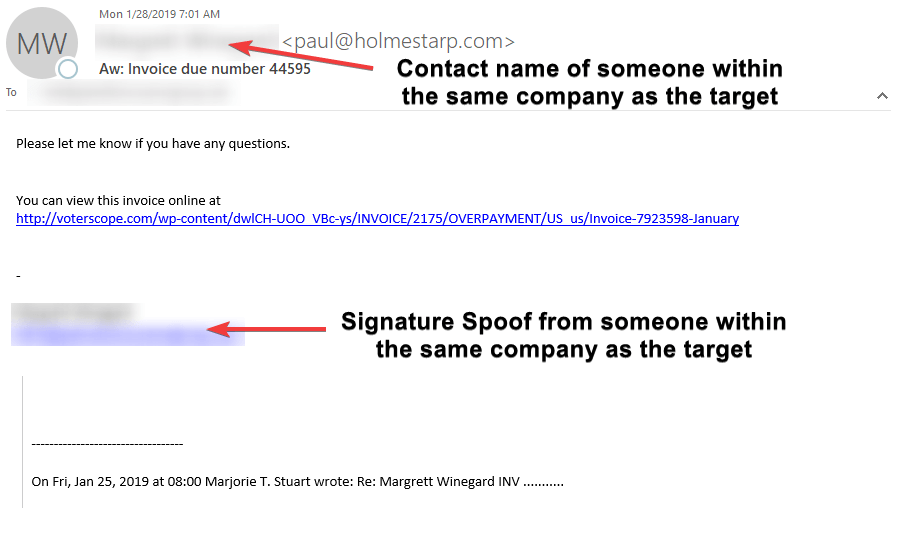
In this example, the attacker spoofed the contact name in the From Address to represent someone within the same company as the target; however, the email address did not match said contact. They did the same thing with the signature but used the correct email address. By adding a spoofed signature, the attacker aims to look more credible in an attempt to deceive the target. Social engineering has proven you're more likely to comply if you know the person.
Also, because invoices are critical in any businesses, this attacker uses this as a hook to get the victim to click on the malicious link.
As we continue, you'll see how these Emotet campaigns evolved.
Example 2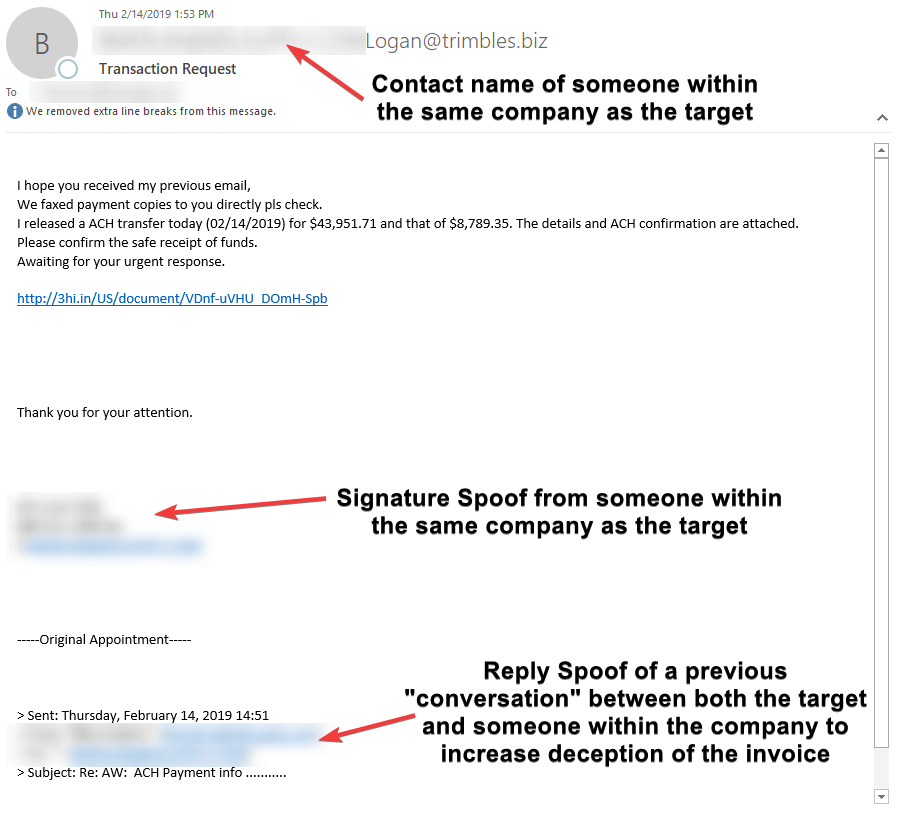
As you can see in this example, the attacker uses some of the same tactics as the first example but takes it a step further by adding a reply chain. This can be effective if the target had communicated with the other person before or deal with numerous emails a day. Keep in mind, the actual From Address did not match to the target's email domain nor did the email in the signature not match the From Address. Even the reply chain did not match - all major red flags.
Example 3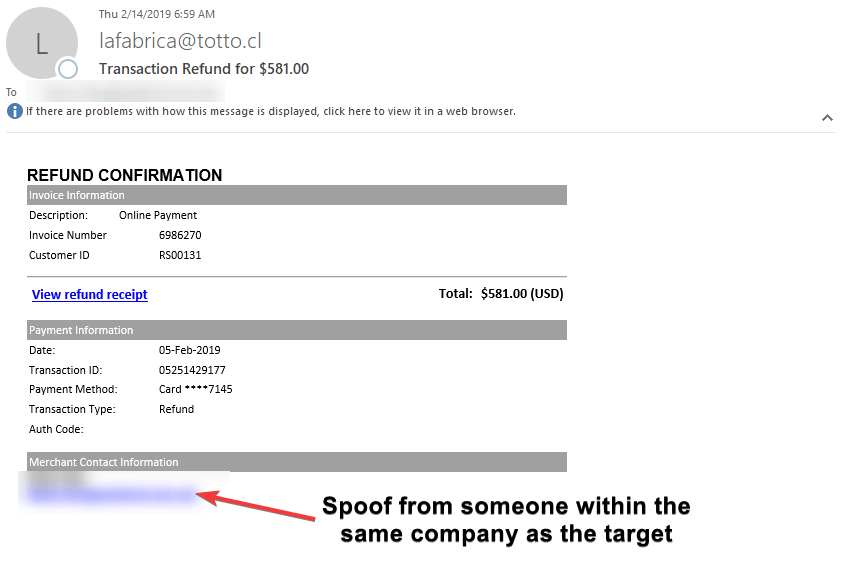
In this example, the attacker used a generic template of a typical invoice that a legitimate business would use. They added someone from within the same company as the target for the contact information. Again, they were aiming to increase credibility that the attached "invoice" is legit and for the company. The From Address had no contact name, which is suspicious as most legitimate businesses will use the business name as the contact name.
Example 4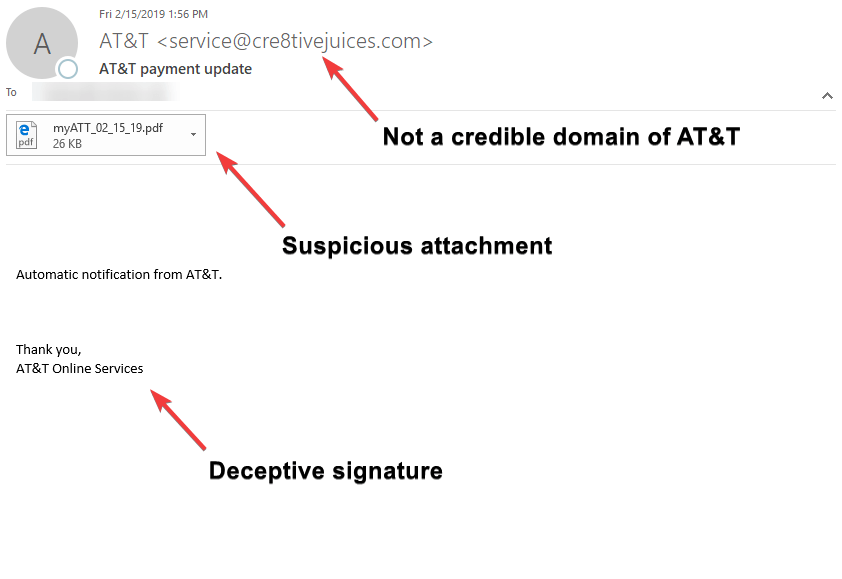
Example 4 includes an attached PDF. The email gives you very little information - the From Address name was AT&T but domain was not legitimate; the body of the email was lacking, only a sentence; and the signature only reads as AT&T Online Service. If I had a red marker to highlight the red flags, the entire email would be red.
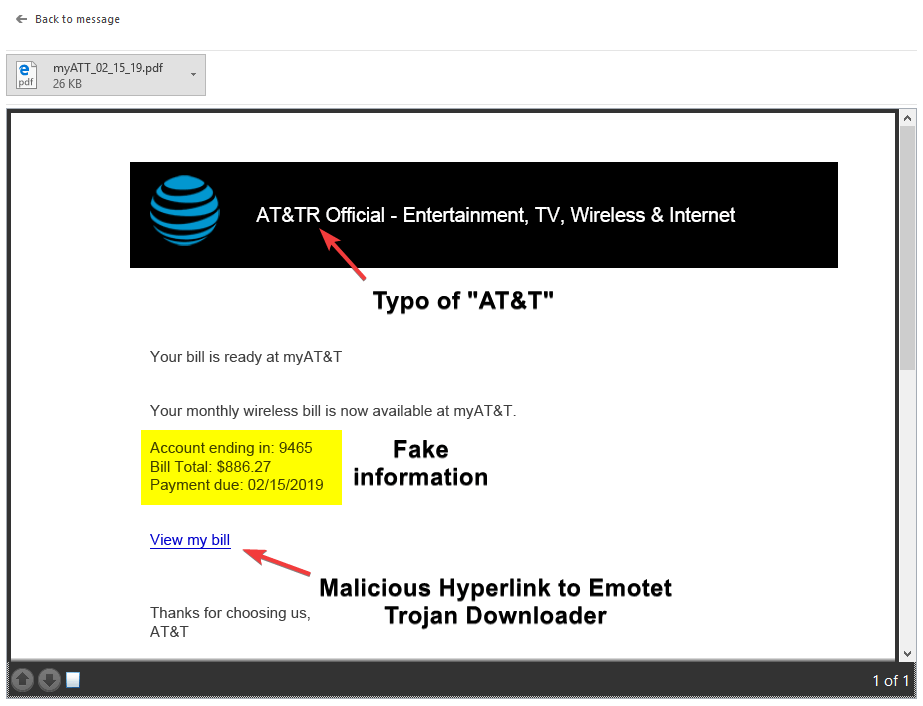
As you can see above of the a one-page PDF attachment, the AT&T logo, though pretty legitimate at first glance, contains a typo. Account information was fake, and, when hovered over the hyperlink, it is revealed the URL did not go to a legitimate AT&T site. This is a classic example of a malspam.
MORAL OF THE STORY
Emotet is evolving and becoming more common. It's critical to have a filtering system that can adapt and evolve to prevent these attacks. It's just as critical to be educated about threats and the best practices to safeguard your organization against them.
Like with any suspicious email, it is always best practice to check the hyperlinked URLs in every email message you receive - no matter how legitimate the email may look. When in doubt, don't click on anything within the message - or, if you have suspicions from the beginning, do not open the email..
If you are an AppRiver customer, forward the email to spam@appriver.com and our 24/7 trained cybersecurity specialists will review the email for your safety.
If you would like to learn more about Emotet, you can find more information in the AppRiver Global Security Report of 2018.
