We Have An APB on CryptoClones
Blog
Thought Leadership
We Have An APB on CryptoClones
Fred Touchette
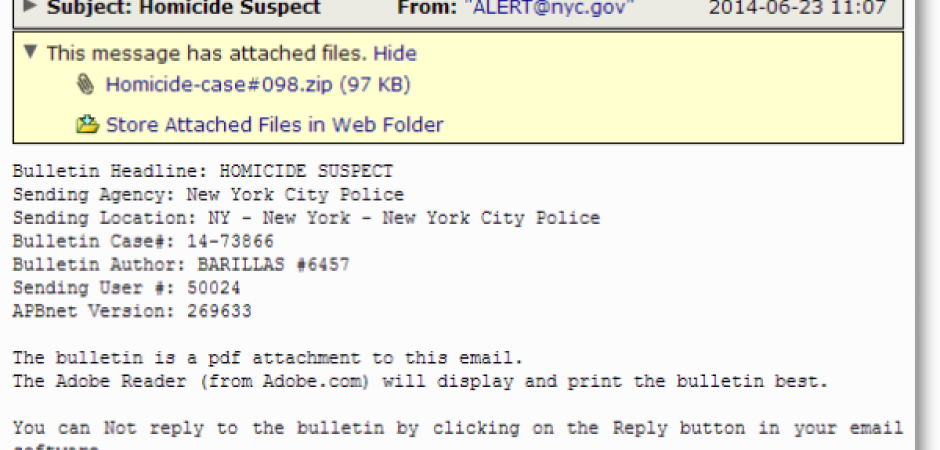
Over the weekend and into this morning we've been seeing a run of malware that uses an interesting technique in order to entice potential victims into falling for its trick. Fear is certainly a social engineering technique that tends to work well and has been used plenty of times in the past. However it is usually used in fake receipts or withdrawal receipts where the attacker is trying to make the victim believe that someone is making purchases on their behalf or simply taking it right from an account of theirs. In this version though the delivery email warns New York City residents of a homicide suspect that is apparently on the loose and possibly on the prowl.
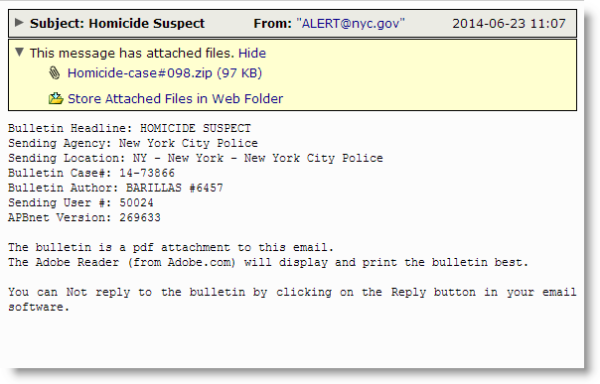
The email says it comes from ALERT@nyc.gov which may or may not be the actual spoofed address that the real NYC.gov website uses to send alerts to those who enroll (and only those who enroll) about events of interest within the city such as power outages, road closures and the like.

This fake alert contains little information and arrives in a simple form text email. In all of the variants we've seen all of the information stays the same except for the numbers under the "Bulletin Case#", and the actual numbers under the following three lines. All of these appear to be randomized.
The malware itself comes in a Zip file and is a screensaver file , .Scr, dressed up to look like a .Pdf that supposedly contains more information about our murder suspect.


Instead of providing this information however, the intended victim will have a fresh copy of the latest CryptoDefense, CryptoLocker Clone. Once the malware finds its way onto its host, the executable Homicide-case#098.exe begins injecting itself into the generic process explorer.exe. It also copies itself into several run areas in order to make removal more difficult.
After it has a strong foothold it begins deleting some very important files and pieces of information the first of which being any Shadow Copies of files the user may have backed up. It does this by utilizing the Volume Copy SHadow Service executable - vssadmin.exe to Delete Shadows/All/Quiet - the quiet supresses any pop ups or warnings that it is happening. A few milliseconds later it also modifies the registry settings to disable system restore altogether.
One potential "flaw" if you want to call it that with these newly popular CryptoClones is that they utilize a hard coded domain which acts as their command and control server. In this case the malware makes an http connection on standard port 80 to contact the domain babyslutsnil.com at the IP 199.127.225.232. If you haven't done so already block all connections to this domain and IP, doing so will prevent the malware from communicating with its C&C server and receiving the private key it will then use the encrypt the victim's computers. Obviously done if this is done after the fact it'll be too late.
These CryptoClones have been very aggressive and highly effective. It is recommended that everyone make strong cold backups of their files and keep them off of the network so just in case someone on their network becomes infected with CryptoLocker et al, things can be repaired. It is never recommended to pay the ransom. This simply encourages the thieves and will certainly mean we will be dealing with these guys for much longer.
