Ready To Click That OneDrive Invoice Link? Not So Fast
Blog
Thought Leadership
Ready To Click That OneDrive Invoice Link? Not So Fast
Bear Huddleston

Recently we posted a blog discussing all the methods Emotet uses to dupe end users.
And, wouldn't you know it, the malicious actors are getting even more bold - using Microsoft OneDrive links in hopes of catching someone with their guard down to click the malicious files.
AppRiver security specialists have seen many of these emails in recent weeks, and though it is similar to most Emotet campaigns, this one uses a different template with a PDF image inserted in the body and resources from OneDrive.
Why OneDrive?So why are they targeting this particular file-sharing service? Because OneDrive is free and easy to create public links to malicious files.
Below are a few examples.
EXAMPLE 1
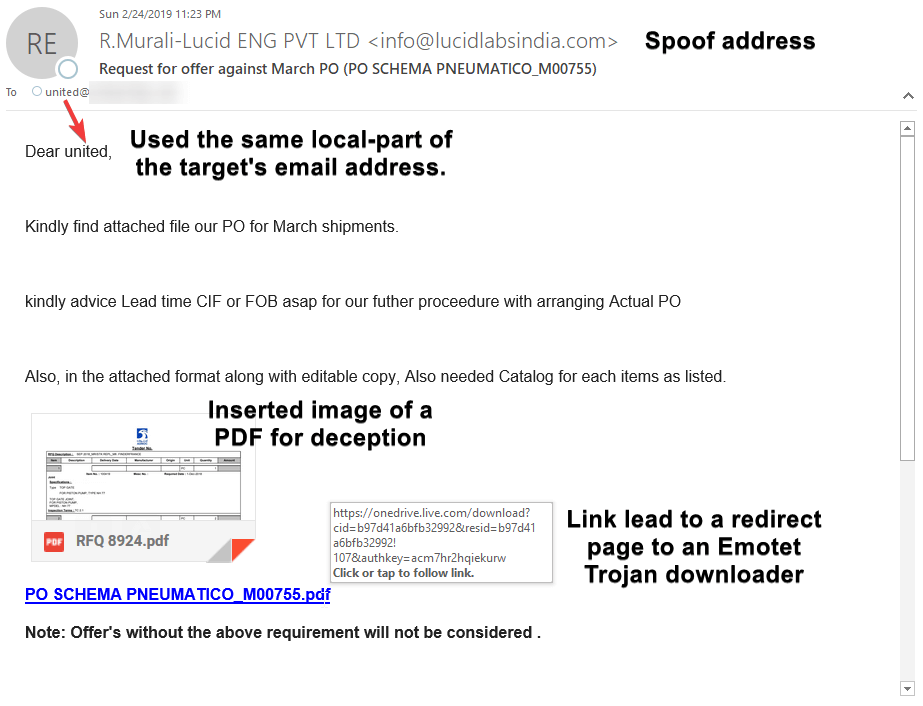
Right away, our specialists noticed several red flags within the email.
First, the salutation used the local-part of the target's email, which is not the norm. Any legitimate business will use first or full name of the recipient.
Next, although not shown in the example, the REPLY-TO address did not match the FROM ADDRESS, leading us to believe FROM ADDRESS was spoofed. Please note, REPLY-TOs can be spoofed as well so it's important recognize other red flags such as the payload.
The final red flag came in the form of an inserted image of a PDF as a hyperlink, same with the name of the PDF. This is a social engineering tactic to build "credibility" with the target. In this email, the payload is the hyperlink of the PDF. As for the hyperlink, it is a OneDrive link that lead to an Emotet Trojan downloader.
EXAMPLE 2
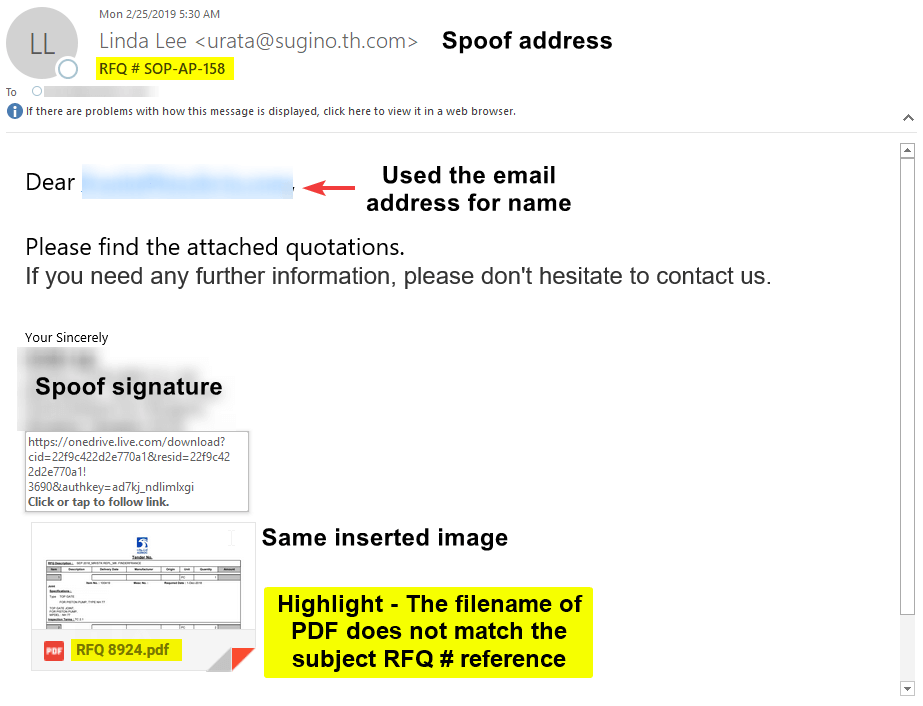
This example is very similar to the previous one, with some minor differences.
The entire email address is used as the name in the salutation. Because of the salutation and the spoofed FROM ADDRESS, we have determined the signature is also fake. More than likely, the signature is copy-and-pasted from a legitimate email the spammer may have intercepted or found in an attempt to add credibility to his malicious email. Interestingly, the same PDF image of an invoice is used in this example as in the previous one, thus leading us to believe we this is a campaign coming from the same individual or organization. One thing of note, the RFQ reference does not match with the subject or filename of the image.
EXAMPLE 3
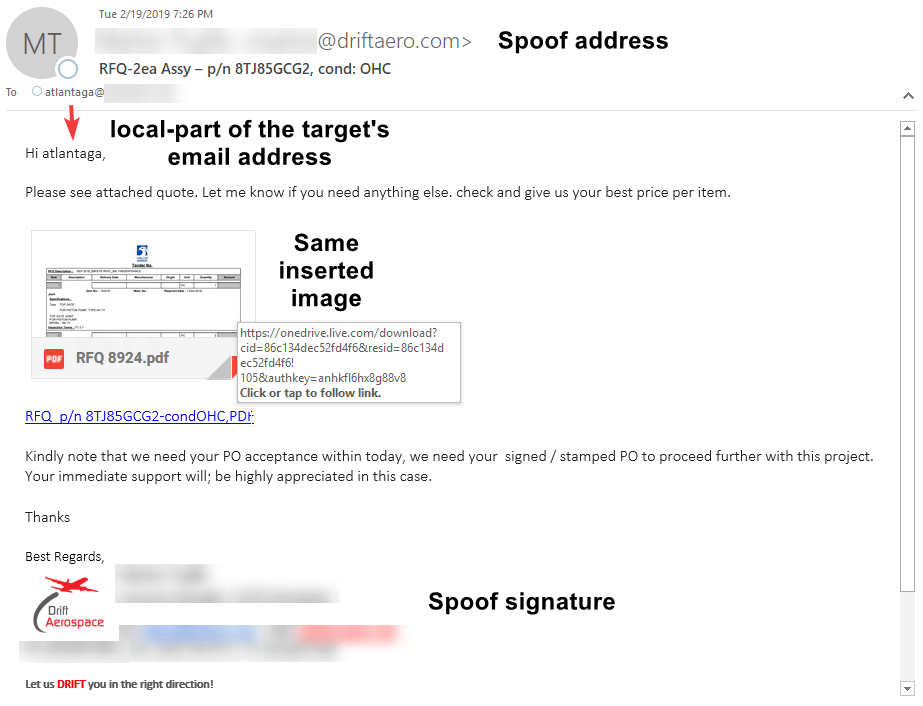
This is a mix of examples one and two. The spammer used the local-part of the target's email address in the salutation. The same PDF invoice imagery is used, so we know it is part of the same campaign. The signature is much more defined in format and style; therefore, the signature has been copy-and-pasted elsewhere. The payload was the hyperlinked image and name of the invoice, which was a OneDrive link for malicious intent.
MORAL OF THE STORY
OneDrive, DropBox, and Google Drive are great services to use for file sharing. However, these services can be used for malicious intent to cause major harm to you and your business. When using these file-sharing services to handle invoices, always be cautious and contact the individual for which the invoice is coming from. If there is any don't, don't click on anything within the message - or, if you have suspicions from the beginning, do not open the email. Always report suspicious emails to your IT or email provider.
If you are an AppRiver customer, forward the email to spam@appriver.com and our 24/7 trained cybersecurity specialists will review the email for you.
If you're not an AppRiver customer, contact us for a free trial of our Advanced Email Security
