GandCrab Ransomware Takes Aim At Your Inbox
Blog
Thought Leadership
GandCrab Ransomware Takes Aim At Your Inbox
Troy Gill

Over the past several days AppRiver security specialists have been seeing early morning Ransomware campaigns targeting users.
The ransomware itself belongs to the GandCrab family and has been the most frequently distributed of its kind over the past year. And like most ransomware, it has the power to significantly cripple business operations if it finds the right target.
In the past 48 hours we have quarantined 260,000 of these malicious messages. Below is a look at the arrival rates for these over the past several days, interestingly the messages have been blasted out in the overnight-early morning hours.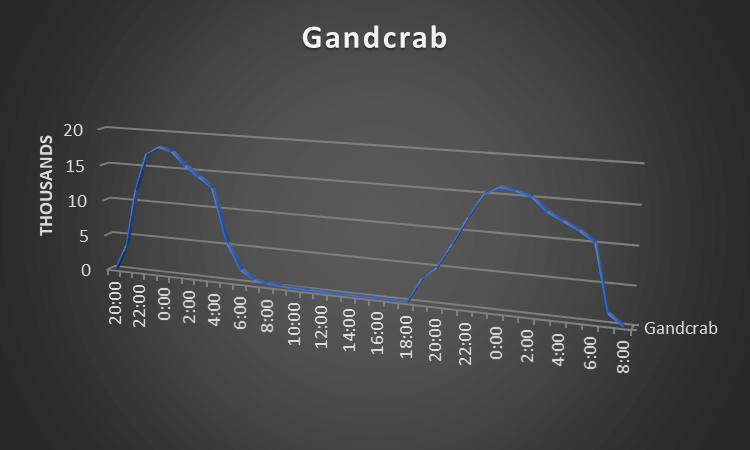
It has been more than a year since the first version of the GandCrab ransomware arrived on the scene. Since then the threat has evolved and already has released more than 10 different versions. Over this past year it has imposed itself as the most prevalent of all ransomware types. As new variants have been released, diligent security professionals have been consistently making decryption tools available online, but this effort is naturally a few steps behind the attacker’s current version. Like all Ransomware before it, it encrypts files and demands payment in cryptocurrency to unlock the hostage files.
CHECK OUT APPRIVER'S GLOBAL SECURITY REPORT FOR 2018
The messages themselves should raise red flags for many as they are very intentionally vague with little content other than the attached malicious payload.
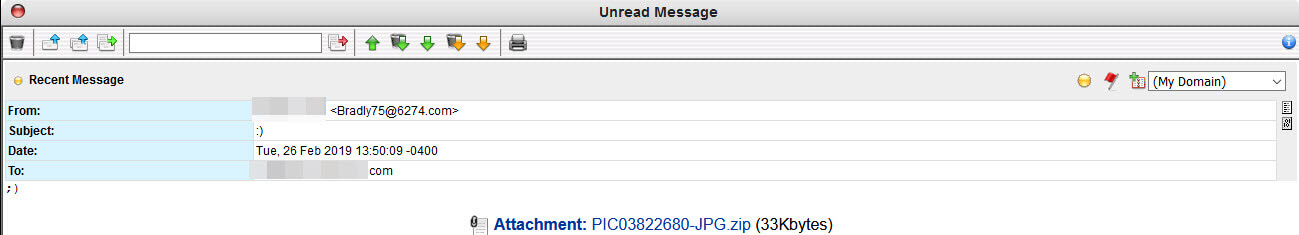
The attached zip contains a JavaScript file that includes JPG (the popular image format) in the filename to dupe the target into thinking they are opening a harmless image. However, if you are paying close enough attention you should notice that the file extension is “.js”.
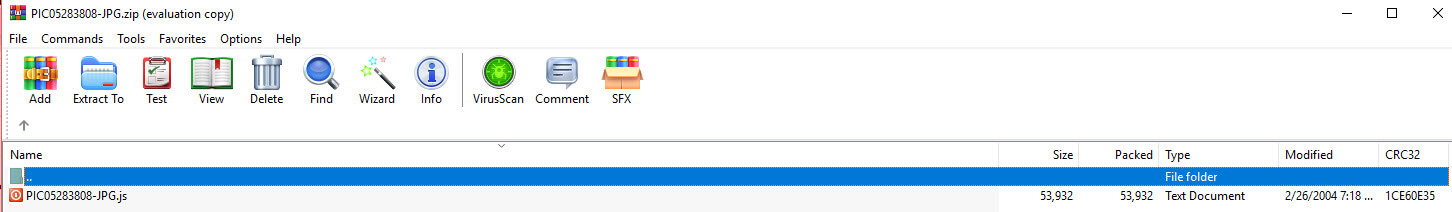
Once clicked the JavaScript launches the Windows component PowerShell which in turn reaches out to an IP located in the Russian Federation to pull down another PE (Md5:abf8b100a5089560ff71f85c55ca3efd).
On execution, the infected system suffers the encryption routine to lock the user’s files. We also observed the malware attempting to locate/steal and existing cryptocurrency wallets on the machine and relay that data back to the attacker. Some but not all these samples displayed indicators that are associated with the Phorpiex botnet, which indicates the attacker’s likely distribution mechanism. Phorpiex has a long history and is known for propagating itself via multiple worm methods.
Of course, all AppRiver's Email Security customers are protected from this threat. However, this is also a good reminder to harden your security posture as much as possible.
In this case, as with so many others, the attacker relies upon PowerShell to complete the infection chain. They do this for two reasons. First it is powerful. Second, by leveraging native functions they hope to fly under the radar of security controls that might see the activity as “normal”. Given this, it is a good idea to disable PowerShell as broadly as possible across your organization. Where it cannot be disabled, consider enabling Constrained Language mode to help restrict access. Also, take advantage of PowerShell logging to help detect when and where an incident might have occurred.
{{cta('993096d6-81be-4b7a-bca6-4eab24d65c14','justifycenter')}}
