Tax Related Email Threats Surge Prior To Deadline
Blog
Thought Leadership
Tax Related Email Threats Surge Prior To Deadline
Troy Gill
We posted earlier in the year about the uptick in email attacks relating to the impending US tax deadline. Throughout tax season, we have continued to monitor tax-themed attacks in the form of bulk-phishing, spearphishing, and malicious payloads. As the filing deadline quickly approaches, we are seeing a large volume tax related messages attempting to dupe users into divulging personal information. Several of the current email campaigns utilize PDF attachments claiming to contain pertinent tax info. These attachments contain links to an active phishing page where attacks lay in wait to collect consumers' personal data.
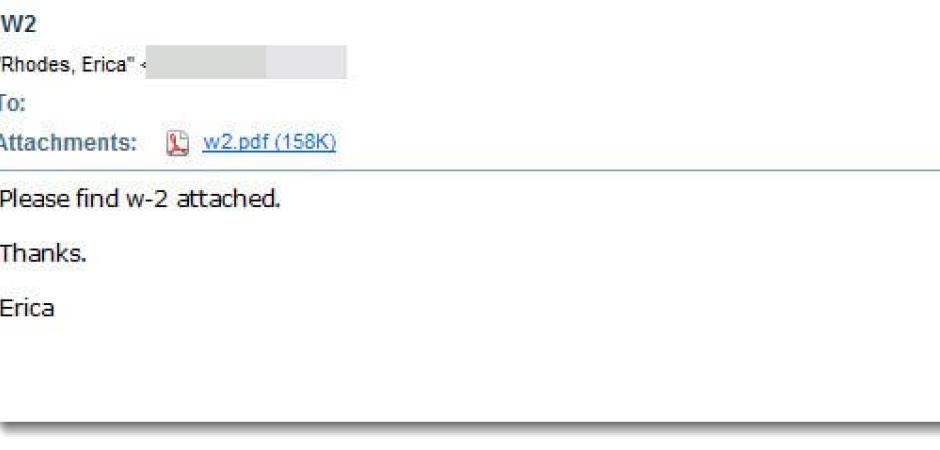
The first comes with a very vague message and claims to contain W2 information.
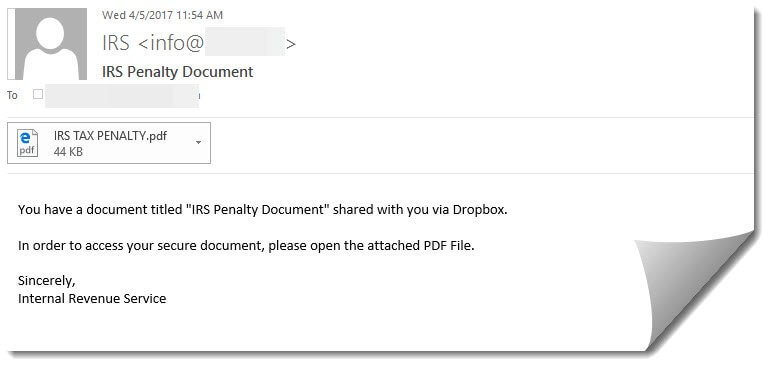
The second email campaign takes a more aggressive approach and tries to startle the user into opening the attachment with the threat of a tax penalty.
Both campaigns are being quarantined currently for our SecureTide™ customers. However, if you are not a customer and you did receive one of these-- then there are a few obvious red flags that should prevent you from falling victim. Firstly, in the second message, we should all notice first that the “IRS” is sending an unsolicited message to us regarding important tax documents. This is not how they operate. Secondly, they will never send and attachment in an unsolicited email. Thirdly, the message states that they shared the document with the consumer via Dropbox (even though the file is directly attached). We think it’s safe to assume that this is also not IRS standard operating procedure. And lastly, though the attackers did insert the IRS into the friendly “from” section, the actual sending domain is not irs.gov.
What else can you do?
There’s no silver bullet when it comes to blocking phishing in general. Attackers are constantly testing new methods and finding what works and what gets to the user’s inbox. But there are some steps an organization can take to try to combat them.
Use encrypted email – Have it be company policy that certain bits of sensitive data should always be encrypted when sent via email. Ideally no information would ever be sent externally, but by following this protocol, the data would still ideally remain secured and unusable by the third-party. Look at the recipient address when replying – A quick glance to the “To:" address when replying could potentially stop many of the spearphishing attacks. Attackers like to use freemail accounts (Outlook, Gmail, Yahoo, etc.) in the "Reply To:" field in a message when phishing. This is only visible to most users once they go to reply. If they are willing to spend a few dollars, they even register domain names very similar to the victims domain. Have 2-factor verification – Having a company policy where it’s acceptable to transfer $50k with a single email request is a bit loose with the coffers. It’s best for everyone if there is a second verification in place such as a quick office visit or phone call. Same with sending around something like all employees W-2 files. Hover over links in messages – Sometimes spearphishing is aimed at just that single email communication to get through to a user and doesn’t need the back and forth. Such as providing a phishing link looking for their email login, linking all the information to do a wire transfer for an external site, or even providing a link for the employee to upload sensitive company data to. Knowing where you are going online by hovering as well as glancing at URLs once you are there is a common security tactic that some people need to follow more closely. Don’t be afraid of your boss – Yeah, this can be a tough one. But some of these spearphishing emails rely on using the CEO name as a strong-arm to get an employee to do something. By writing the text in a way that sounds urgent or demanding, some employees may forgo any set policy and bypass procedures in place to please their boss. After all, they think the CEO is ordering them to. Obviously questioning every order that comes down isn’t feasible or advisable, but again there are certain things like sending W-2s and wire transfers that should have set policies in place where everyone follows them no matter what. It’s better to question all wire transfers than to miss that one and send $20k to some foreign account. Use an email filter – This can be the obvious one here. But many email filters have some advanced features and tests that can catch these sorts of attacks that people may not be aware of. At AppRiver, we have an advanced spearphishing test that can look for these types of low-key phishing email tactics and stop them. If you have a filter service that doesn’t have spearphishing features in it, you can even do something like block external email using your domain name in it, so that any email using your domain name, but coming from somewhere that’s not your own server, gets blocked.