That's No Executable
Blog
Thought Leadership
That's No Executable
Jonathan French
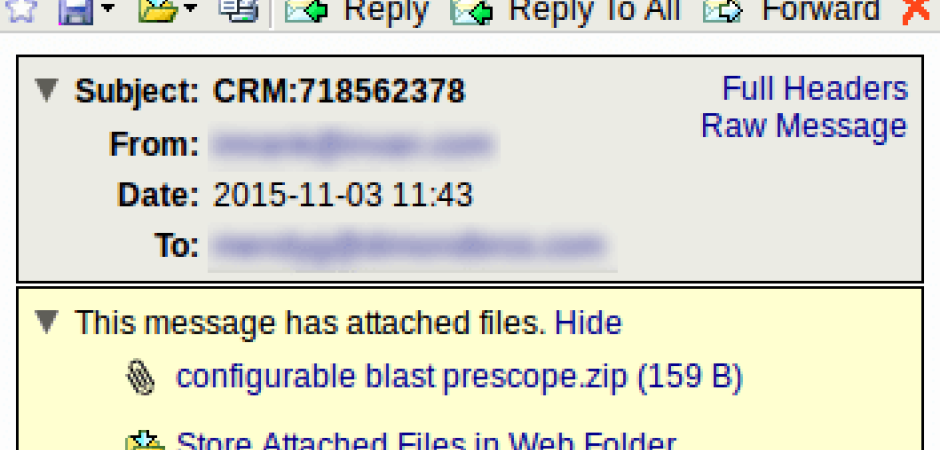
We just had a small campaign of zipped exe files coming in as attachments in messages asking users if they would like to "place your order today". Plain text emails en masse with attachments is usually a dead giveaway for malware campaigns so these are easy to spot. The first interesting thing I noticed though was that the campaign was coming in with two different files. Now that's pretty normal for some campaigns to use slightly different executables in each message, or in this case use random file naming, to make an attempt to avoid detection. But the interesting thing was that one of the files was being caught by an old virus rule from April (about 60k hits so far) but the other one looked to be significantly different. With one file being a relatively normal 33 kilobytes in size and the other being just 159 bytes total, that's a huge difference.
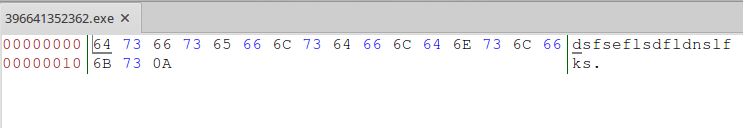
So first thing I noticed was the file size but before even seeing what's in the small zip, I have a pretty good idea that this file is inert and can't do anything. A zip file that small essentially means it contains almost nothing given zip headers alone probably make up most of that size. We see some broken files every now and then but usually as one offs and not in the thousands. Upon unzipping the file, you are actually presented with a .exe file. This 'executable' being only 19 bytes is again a clear indicator it's not really an exe. When checking inside the exe, there's just a random looking string of "dsfseflsdfldnslfks". Looking at the characters and their placement on a keyboard, my guess is the string was hand typed by somebody. Which leaves me thinking an attacker accidentally sent some wrong files for part of the campaign.