Fake JP Morgan Secure Emails
Blog
Thought Leadership
Fake JP Morgan Secure Emails
Jonathan French

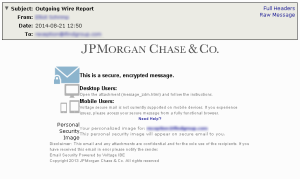
A campaign just started up of fake JP morgan emails. The emails coming in claim to be secure messages from JP Morgan using the Voltage secure messaging platform. The FROM name changes between the messages but stays in a consistant format for the actual email address (First.Last@jpmorgan.com). Interestingly, all of the messages seemed to try to use the same security image of, what I assume, is a valid users image from JP Morgan. However the link the spammers used appears to be dead now and none of the messages show a security image.
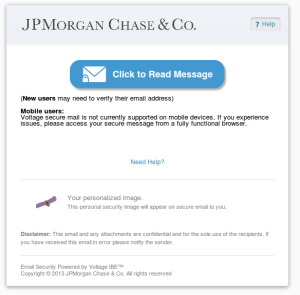
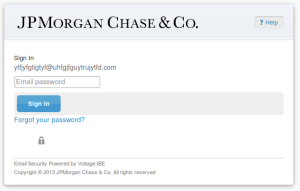
The HTML file is just an official looking page with a button to read the message (and a personal image here that shows). One thing to note is that looking at the source of the HTML or hovering over links does indeed only show jpmorgan links. The Click to Read Message button did not show the link when hovering and linked directly to an address using an IP instead of a hostname.
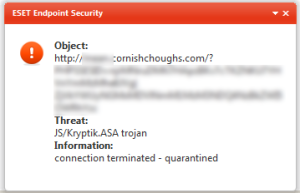
This campaign has sort of a 3 part attack going on here. The first attack is when you click the read message button. The next page it loads has a malicious iframe in it. From the samples I have seen, the iframes all had data hosted at cornishhoughs.com. Eset classifys the attack as "JS/Kryptik.ASA trojan".
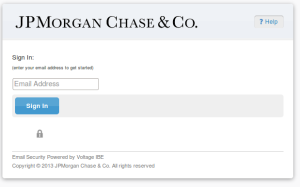
No matter what you type in, as long as it's in the proper format, the page advances. This could be considered a second part to the entire attack. The pages do make POSTs to the server with the email address and password that are typed in. This data is most lilely being harvested as well for further attacks to be made with that users information. If anyone visited these pages and typed their information in, I'd strongly suggest changing your password as soon as possible.
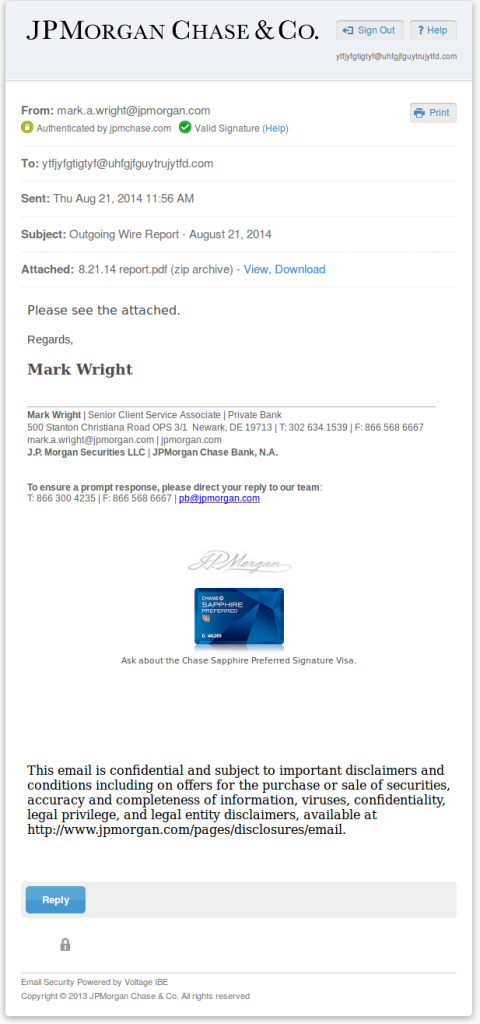
Once you get this far you are taken to a rather convincing looking secure messaging portal. Complete with working buttons that all lead to JP Morgan pages. The exception being the View and Download buttons.
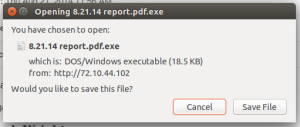
Clicking either View or Download prompts you to save an exe file with a double extension at the end and is the third part of this attack.
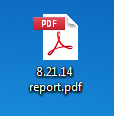
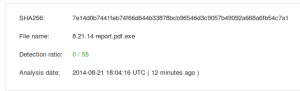
These can fool most users in to thinking they are harmless once the file is saved. The reason is that most of the time the malware writeers will build in a resource icon of whatever the fake extension is. This method combined with the fact that Windows does not show known file extensions by default, means that the average user would only see "8.21.14 report.pdf" as the filename and a normal PDF icon as well (as seen below). Some users find it annoying to show all file extensions but it can make it significantly easier to spot the double extension files that trick users.
At the time of checking all of this, VirusTotal shows no AV company has anything on this file. It appears to be a trojan downloader that retrieves content offsite. Fortunately we were able to quickly block the file in our filter and have over 177,000 hits so far and climbing.
This particular campaign was tricky due to it being rather in depth and the effort put in to make it convincing. This type of campaign takes more resources for an attacker to put together, but if successful it can yield more of an impact due to the threat not being as obvious.