Mailbox Scams Ramping Up
Blog
Thought Leadership
Mailbox Scams Ramping Up
Bear Huddleston

Online mailbox scams aiming to trick users to hand over their mailbox to a scammer have been ramping lately.
The scam begins with a deceptive email to the end user claiming suspicious activity has been observed in their email account or that their inbox is full and needs attention. The email also contains a link that is surely malicious and an effort to gain the user's credentials.
Don't be fooled by this phishing attempt.
Below are several examples to watch out for.
EXAMPLE 1
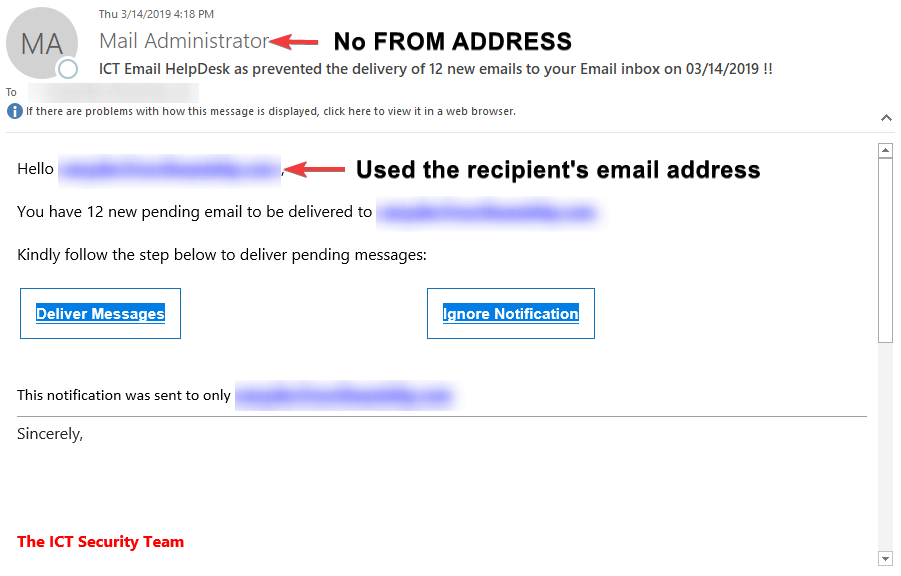
In this example, it appears as if the email is from the recipient's HelpDesk, which if you work for a company that has a HelpDesk or any IT department this could seem legitimate. However, one should note that the FROM ADDRESS does not include an email address, which is highly unusual. Also, the salutation used the recipient's email address and not their name. Normally, the IT department would address you as your full, first, or last name. Also of note is the formatting of the email - there are too many wasted spaces at the signature and the color around the two buttons were not filling the actual box. These small details should add to your suspicions about the legitimacy of the email.
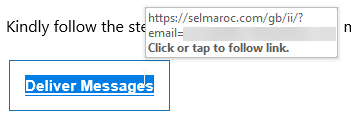
As for the payload, the links the scammer wanted you to click, it does not go to a legitimate HelpDesk or webpage. A legitimate email would use your company's domain or recognizable emailing service such as Office 365.
EXAMPLE 2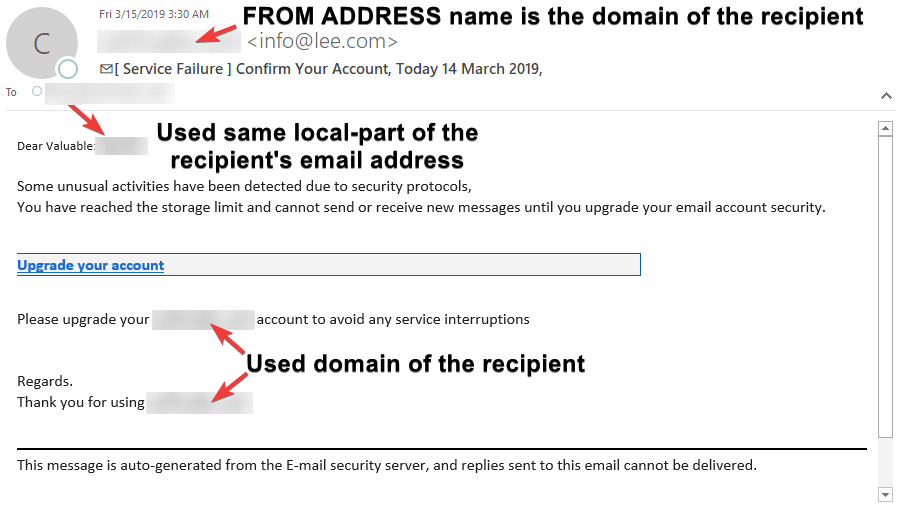
In this example, the email alerted the recipient of suspicious activities and storage limitations of the mailbox. It's unusual to see both alerts in one email; especially one about security and the other storage.
Other red flags include:
FROM ADDRESS name was the domain. The local-part of the recipient's email in the salutation. The odd use of language that involved the recipient's domain.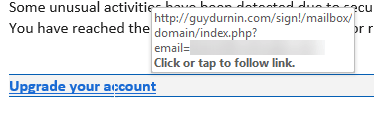
Note the payload did not go to a legitimate website. You can spot these exploited sites in email if you see "/index.php?email=" in the link. It's very common for these type of scams.
To get more depth, question marks in URLs is a Query string. It can pass key-value -in this case, your email - to the server-side. This would build a database with your email and username/password for the scammer. Please note, Query strings are not inherently malicious. Its purpose is to help recipients and businesses connect directly and easily through links.
EXAMPLE 3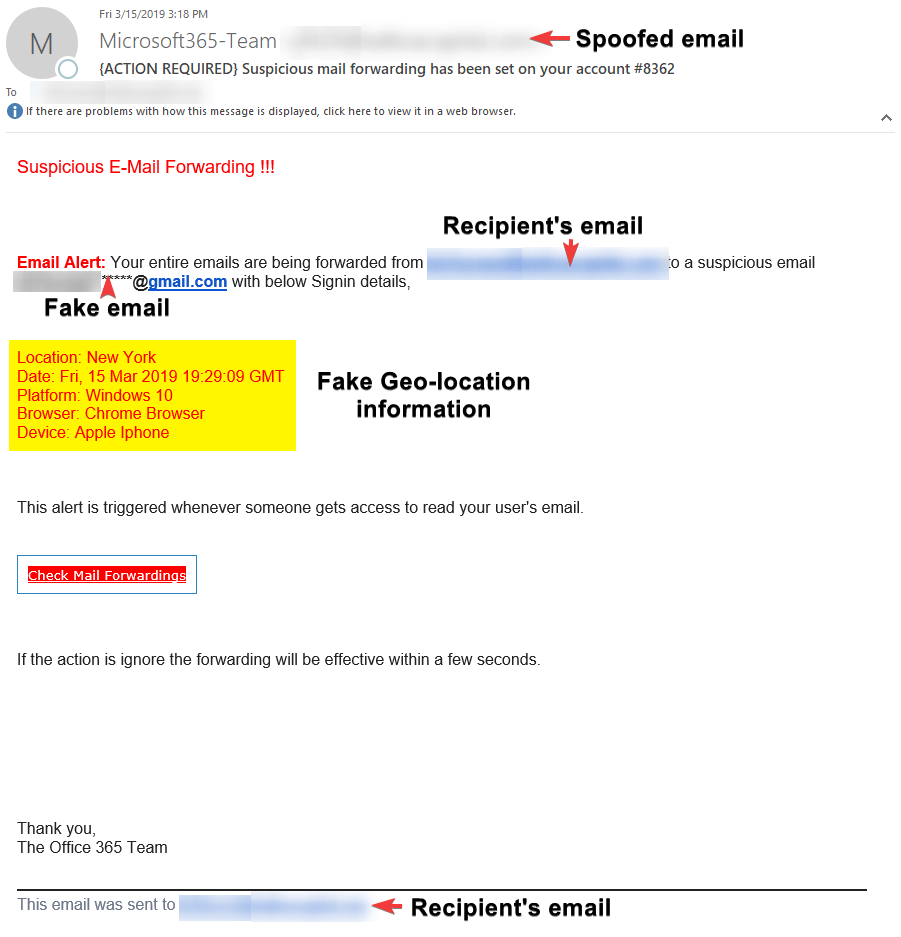
This example email was more deceptive. The scammer spoofed the email as Microsoft and using the same domain as the recipient's email. They used a fake email that has the local-part of the recipient. They even added a fake geo-location where the mail box was "accessed." However, like the previous example, the formatting of the email was off, too much empty space, no full boxes, colored fonts.
.png.png)
The scammer used a similar payload as the others with the only difference being "?userid=" which function the same as "?email=" because it's telling the scammer who is clicking on the URL.
MORAL OF THE STORYBe aware of these scams and become familiar with your mailbox. Know which email service you are using. If you are not sure, get in touch with HelpDesk or your IT department. ALWAYS be cautious with emails asking for you to click on link to allow/prevent an action or provide your username and password.
If you are an AppRiver customer, forward any suspicious emails to spam@appriver.com and our 24/7 trained cybersecurity specialists will review the email for you.
If you're not an AppRiver customer, contact us for a free trial of our Advanced Email Security
