Business Email Compromise Attacks via Name Impersonation
Blog
Thought Leadership
Business Email Compromise Attacks via Name Impersonation
David Pickett

Name impersonation attacks have exploded in popularity over the past few years. They cost malicious actors little time, infrastructure, or sophistication. The FBI's Internet Crime Complaint Center recently reported over 900 complaints a day in 2018 and $2.7 billion in American losses alone.
It's extremely simple for attackers to harvest names, titles, organizational details and their email address naming convention by scraping the target company's website. This information can be combined with other open source intelligence obtained from social media. With this data, attackers tailor impersonation attacks towards specific targets.
The attacker simply utilizes a legitimate display name employees would recognize. These attacks are more likely to succeed when the recipient views the message on a phone. By default, most phones do not display the email address of the sender, they only show the display name.
There are a wide variety of attacks conducted via name impersonation - gift card scams, wire transfer fraud, invoice fraud, changing payroll direct deposit information, and even estate fraud. In this blog we'll take a quick look at a some of the more common name impersonation scams.
Gift Card Fraud
The most common name impersonation attack theme is via gift card fraud. Since gift cards can be easily be sold, traded, or used for money laundering, to an attacker they are almost as good as cash.
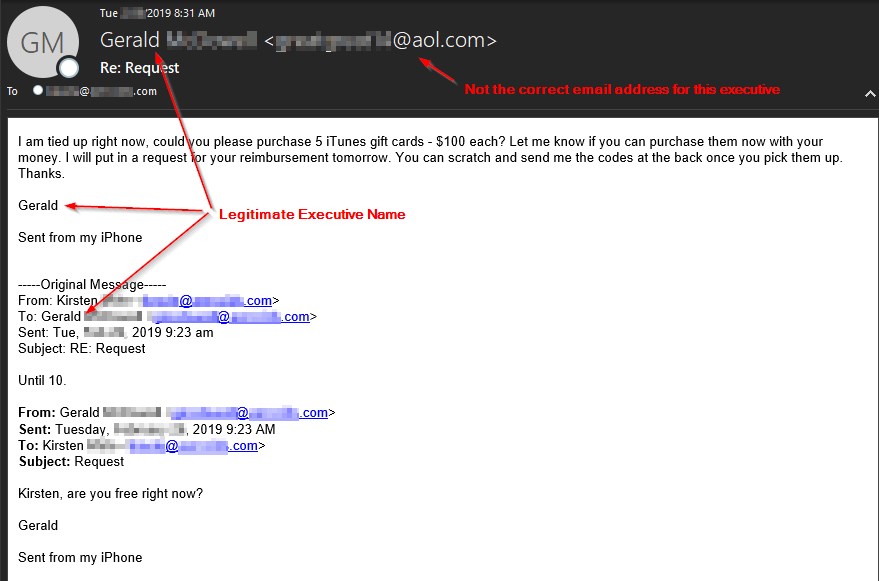
First example:
The attacker usually begins with an initial generic phrase such as, "Are you available right now?" If the target replies back, the attacker either proceeds with the gift card instructions via email or attempts to transfer the conversation to text messages. Moving the follow-up conversation to text messaging is a deliberate attempt to avoid email filtering.
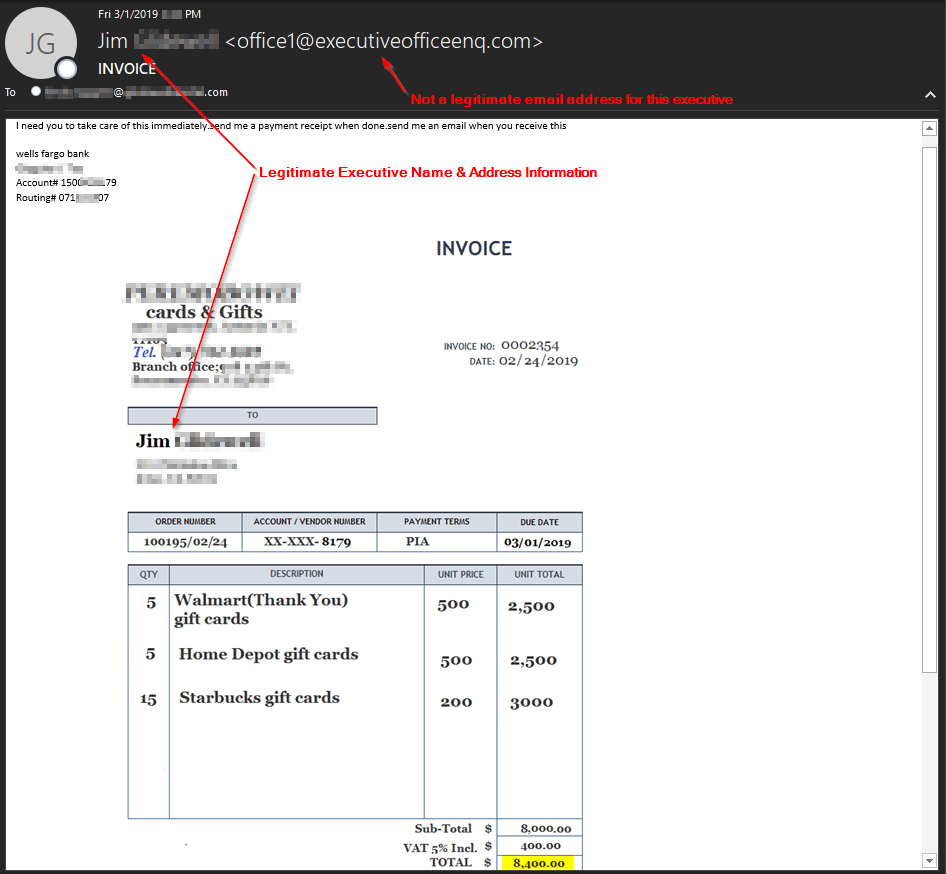
Second Example:
This attacker spent a little more time. They created a fraudulent invoice image in the hopes of adding legitimacy. They also added European Union value added tax (VAT) to the invoice. However, VAT wasn't applicable for this particular transaction.
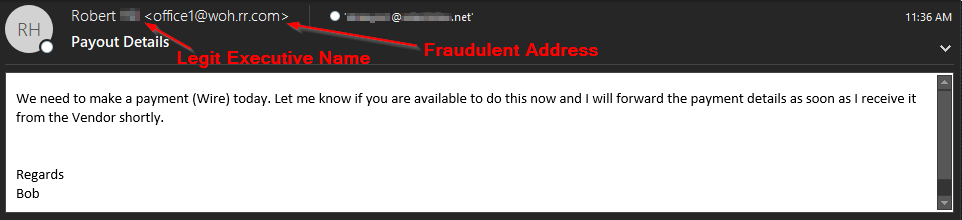
Wire Transfer Fraud
This is a simple example of how one of the common wire transfer fraud attempts begin. Attackers impersonate the name of an executive and typically target finance or HR staff for these. They commonly create a sense of urgency as phishing emails that invoke fear or urgency achieve better results.
Invoice Fraud
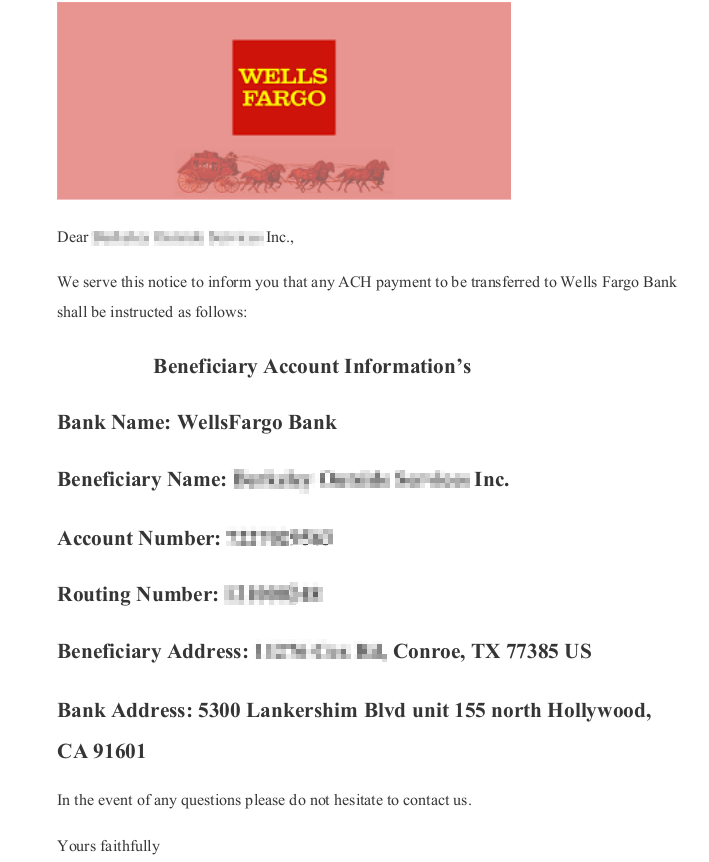
Many times attackers will attach a .pdf file containing instructions on modifying wire transfer or ACH payment information. This is to add a sense of legitimacy and attempt to evade some email filters which have trouble extracting information within a pdf.
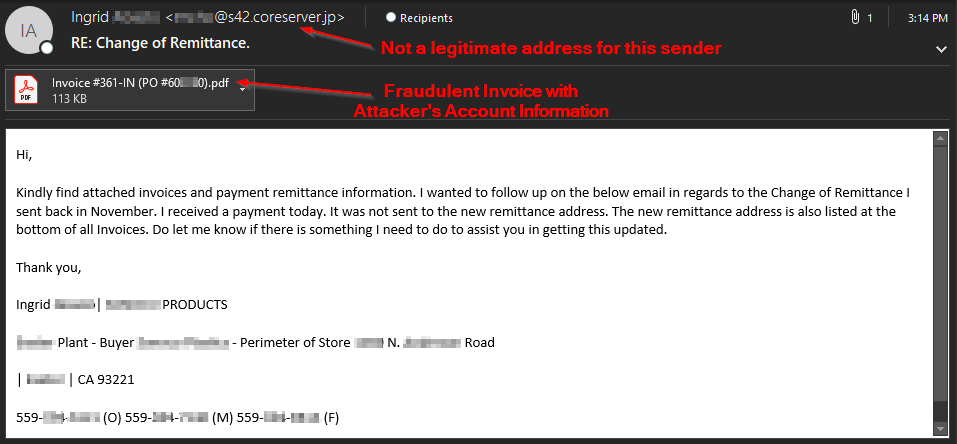
When viewing the attached .pdf, a suspicious Wells Fargo logo is evident. This attachment is an attempt to deceive the recipient to update their ACH payment information for future invoices. This way future payments for invoices route to the attacker instead of the legitimate bank account.
Payroll Fraud
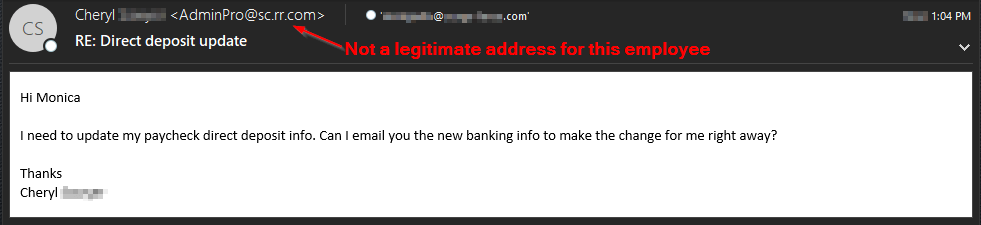
We've seen an increase in attackers attempting to target HR and Finance staff for updating payroll direct deposit information. By doing this, attackers can masquerade as any employee in the organization for the fraudulent activity, not just an executive.
Estate Fraud
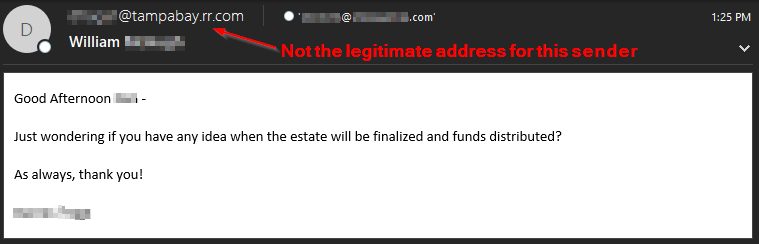
This example shows attackers attempting to solicit information regarding estate distributions so they can better direct their attacks at the perfect moment. As we commonly see, attackers have no qualms directing scams toward anyone at anytime as long as they can turn a profit.
AppRiver Impersonation Protection
Our email filtering security team has a variety of rules for our global tests scanning for these attacks. We believe defense in depth (layered security) is the best protective posture to maintain. We've also added a feature in our customer portal which provides administrators the ability to block display names (and even similar variations of them using a Levenshtein Distance). The administrator may tag the subject or even block these messages outright if they utilize an internal users display name. Below is a quick video that highlights this helpful feature to further mitigate these display name impersonation attacks.
To ensure you are protected against phishing and malware attacks - contact us for a free trial of our Advanced Email Security
