Adwind RAT infestation is trending up
Blog
Thought Leadership
Adwind RAT infestation is trending up
David Pickett


Malware as a service is exploding in popularity, this allows it to be distributed openly as a service by the creators. "Customers" pay a fee for the usage of the Trojan just as businesses would for cloud provided services. This essentially allows anyone to purchase the Adwind Remote Access Trojan (RAT) for a small fee, regardless of computer skill. Recent examples we've blocked utilize .jar (java archive) files or .jar files inside .zip files.
More about RATs & Adwind
IT staff's ability to remotely resolve a user issue is a legitimate example of remote access tools. However, malware authors also utilize them for nefarious purposes, we term these Remote Access Trojans. They allow the operator to steal credentials, record keystrokes, take screenshots, access webcams and microphones, modify files, execute code and drop malicious programs on the machine. Many Trojans, such as Adwind, are environmentally aware. The examples we've researched display the ability to detect that it's running in a virtual machine. Furthermore, it may upload computer name, machine information and cryptographic machine guid to command & control servers. This allows the controller to tailor the malicious programs it downloads specific to the machine type. It uses Java, therefore, it could possibly run and download malicious programs on any supporting platform (Windows, Mac OS, Linux, Android, etc).
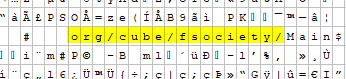
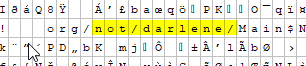
Humorous Mr. Robot ReferencesMalware authors and distributors definitely have a sense of humor. Two last week that gave us a laugh included references to the Mr. Robot series in their java .class naming. Below are raw hex snippets from two different examples, at least this malicious author isn't Darlene!
Zero-Day Adwind Variant
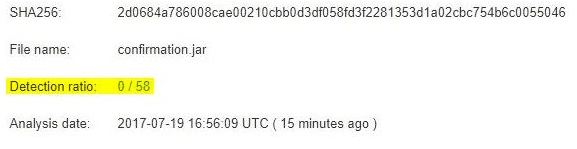
We were the first to implement rules to block a new variant which caught our attention Wednesday. At AppRiver, our SecureTide spam and virus filtering team works 24/7/365 to protect our customers from these types of threats as they emerge.
The packet capture of this example shows it reaching out to two different hosts while being analyzed: 37[.]72[.]175[.]150 on port 800 & 2[.]21[.]75[.]64 on port 80.
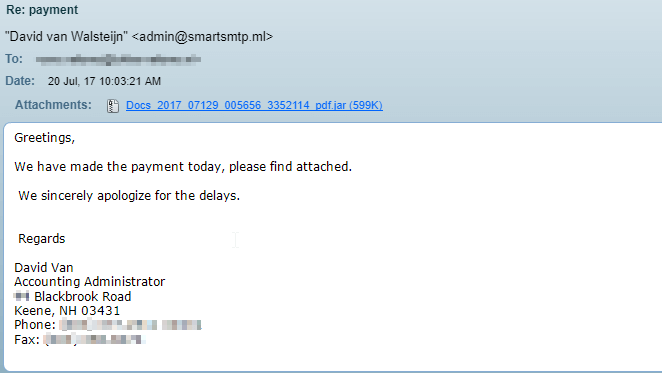
A Few of Today's Examples with Adwind Attached: