Hancitor Picking Up Steam
Blog
Thought Leadership
Hancitor Picking Up Steam
David Pickett
The Hancitor (aka Chanitor & TorDal) malicious downloader has been picking up steam.
Creators actively refine code to a sophisticated downloader increasingly able to avoid detection. This requires a user to run an infected Word document containing malicious VB macros. Upon doing so, Hancitor pulls DELoader (Terdot) - a financial information stealing malware. These malicious downloaders essentially allow the controllers to install anything on an infected machine. The malevolent payloads Hancitor opens up the door for has evolved, and will continue to do so.
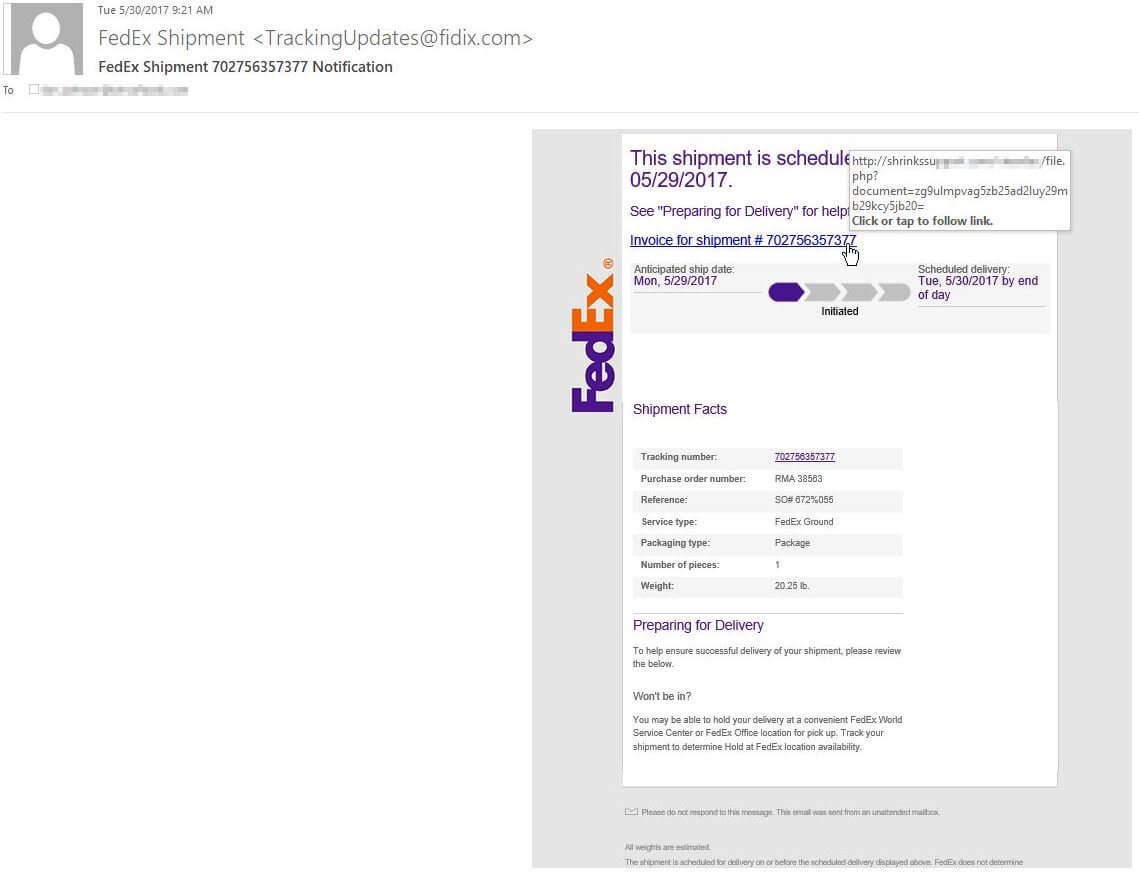
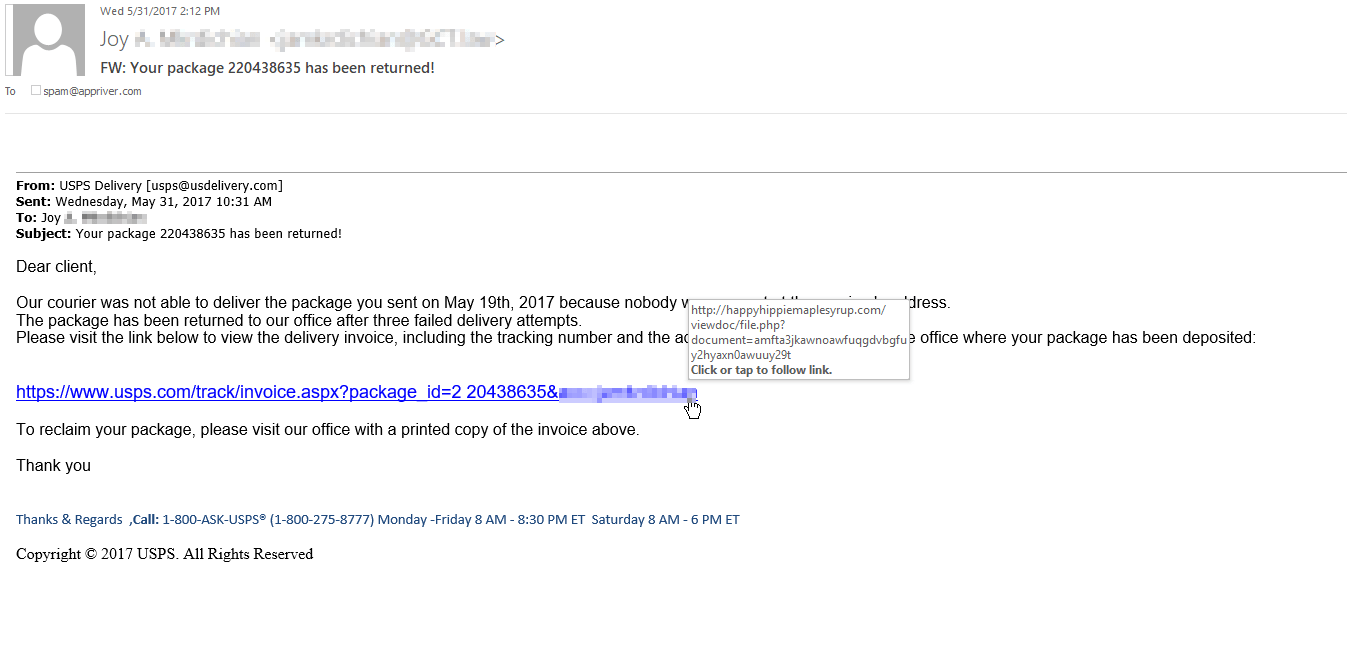
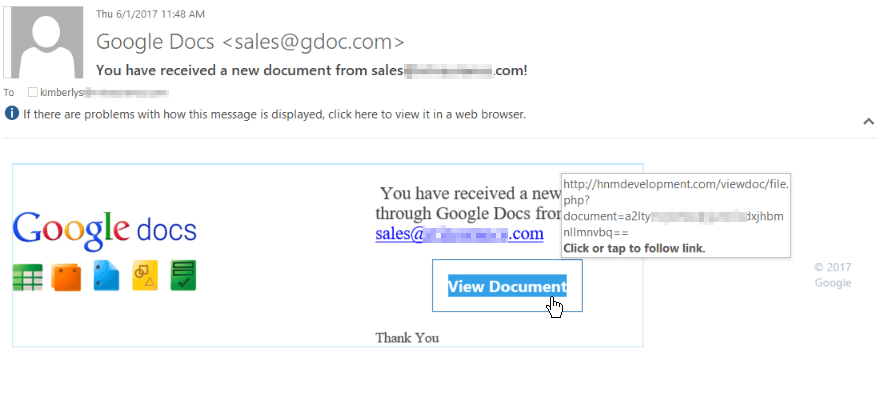
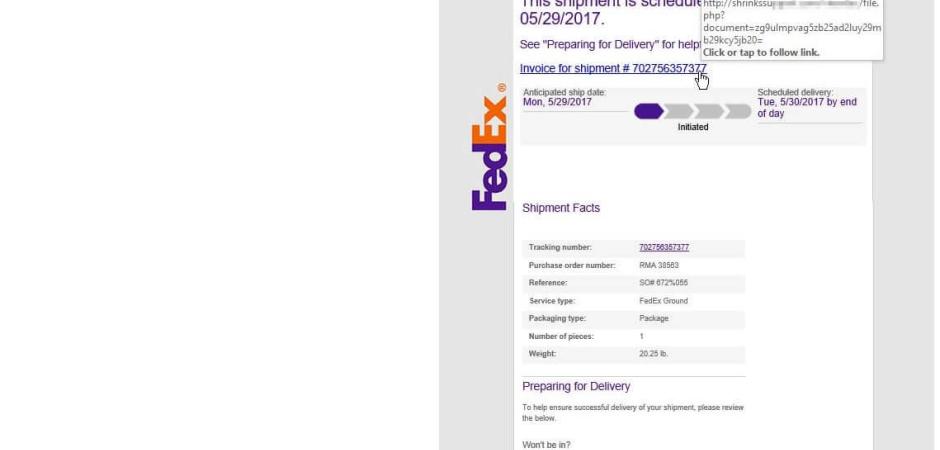
Fake FedEx, USPS, Google messages targeting inboxesWe've seen multiple variants offered via a variety of different fake emails. Campaigns varied from generic fake invoices and incoming faxes to spoofing larger companies such as ADP, Comcast, Delta, or DocuSign. This week it's been fake FedEx, USPS, & Google Docs messages.
FedEx example The sending address may be spoofed but in this example it is from fidix[.]com (not fedex.com). Also when hovering over the hyperlink it does not point to FedEx's site. For this campaign there were a few different sites the link points to. USPS example Again, sending addresses can be spoofed. However, the from address of usdelivery.com is not a legitimate USPS site. The hyperlink examples change but Happyhippiemaplesyrup[.]com is not affiliated with the USPS. To see the the hyperlink information, hovering over what purports to be a usps.com link. Google Docs example Although not the true sender, gdoc[.]com is not affiliated with Google and the link address points to hnmdevelopment[.]com. Links lead to Hancitor malicious contentThe links in these emails lead to a download of malicious Word documents.
Below is an example Word document of what the USPS variant pulled in. A Word document that gives you instructions on how to run it should set off red flags.
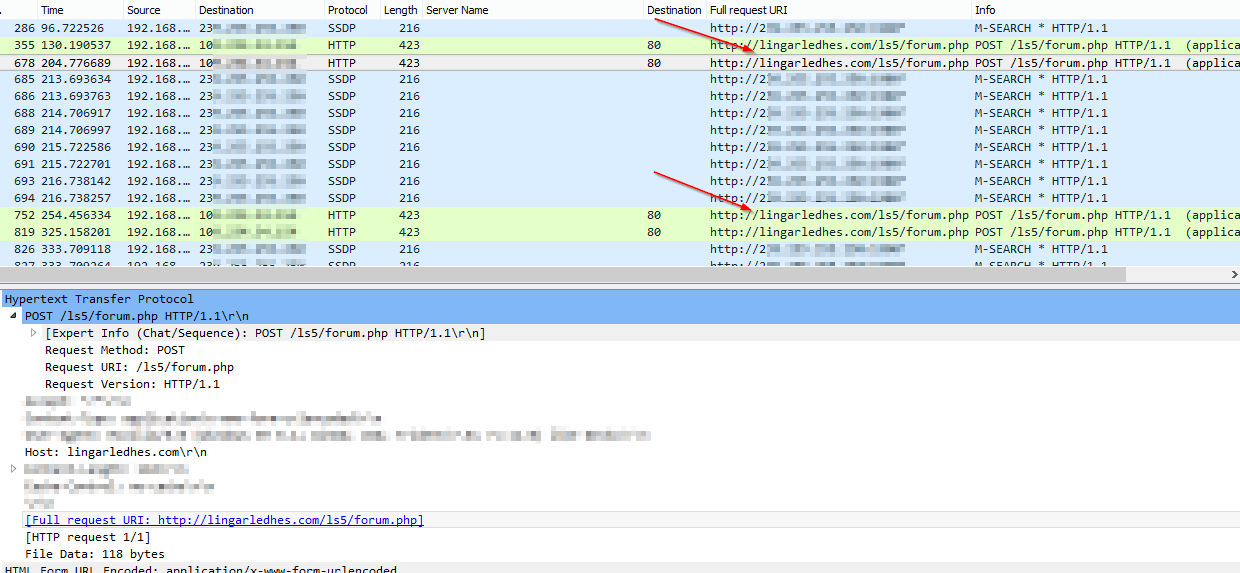
After Enabling Editing and Enabling Content (red flags) for this malicious document, I captured a Wireshark packet capture of the infection posting my test machine data to one of the command and control servers at lingarledhes[.]com. This allows the C&C operators to tailor malicious downloads per machine type, geographic location, and any other variables they choose. Below is a brief snippet from the beginning of the capture.
End users should be cautious when dealing with Word documents that contain macros, especially when they originate from external sources. Many businesses must use Word macros, and we understand that. However, if feasible, we recommend administrators implement a group policy to disable Word macros.
At AppRiver, our SecureTide spam and virus filtering team works 24/7/365 to protect our customers from these types of threats as they emerge.