SpearPhishers Reeling in Tax Returns
Blog
Thought Leadership
SpearPhishers Reeling in Tax Returns
Jonathan French
It's that time of the year where tax forms are filed and (unfortunately) personal information is sent around via unencrypted email. Internal email, that is email between users in a company on their own email system, can be considered as secure as the server itself for the most part (which one may interpret the degree of security as she chooses). If an attacker can't get access to the system, he will target those who have access. Some employees may place a little too much trust in their internal email processes and can fall victim to spearphishing attacks that appear to be other internal users emailing them.
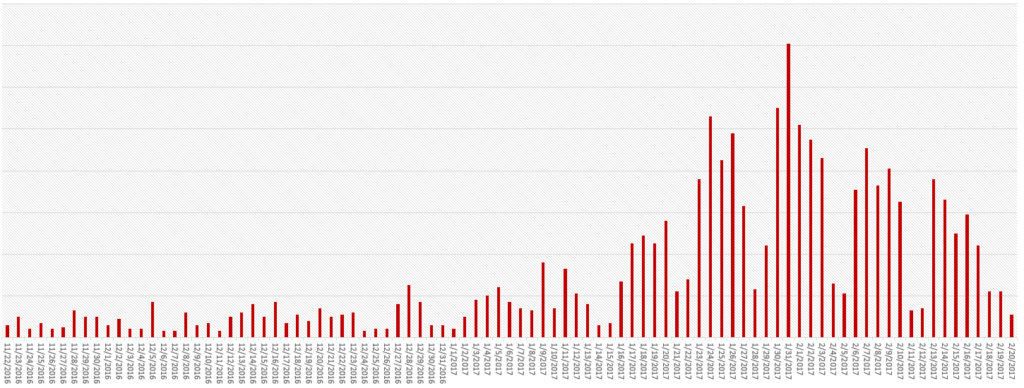
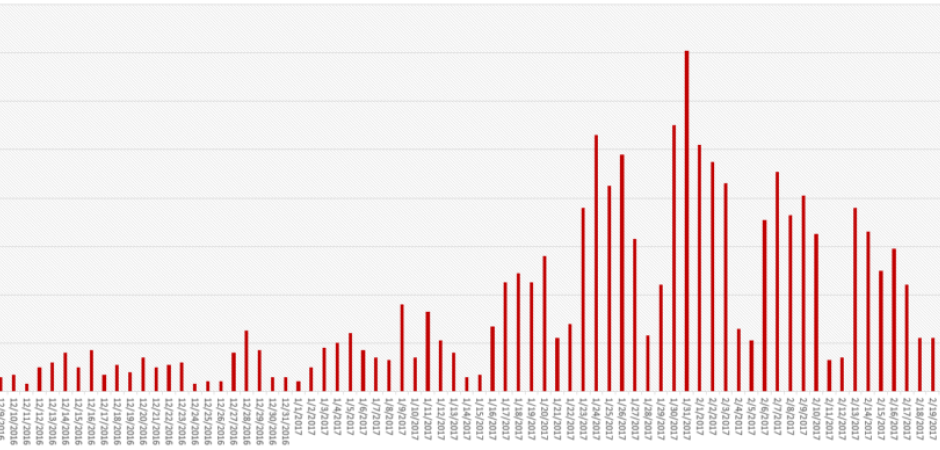
One especially trying time of year for these types of messages is during tax season. January to mid-April is the prime time for attackers to try to convince susceptible employees to hand over private company information, including: tax returns, company bank account information, and employee information including healthcare and W-2 files. Many organizations naively believe that this could never happen to them. However, a quick search online can usually show the prevalent dangers of these sorts of attacks. Companies like Snapchat, Seagate, Polycom, Advance Auto Parts and, yes, even hospitals, schools, and utility companies have all been victims of spearphishing.
At AppRiver, we have seen the spike in phishing traffic already occurring in 2017. As the beginning of the year is typically when taxpayers anticipating big returns are mostly in a rush to have their returns filed, while taxpayers who will owe usually procrastinate until the last second, we anticipate that phishing traffic will continue to dwindle until the very end of tax season, with perhaps another small push towards the deadline.
When an outside attacker is able to craft an email in such a way that it looks to be internal, some users will trust them without digging deep enough. And that's the core component to spearphishing. An attacker doesn't need to be a hacker or gain access to secure internal systems. If someone can send convincing, legitimate-appearing emails to users, they may just hand over that sensitive information none the wiser. There are some small details astute users can decipher to notice spearphishing emails, but more often than not they are hard to catch just reading them at face value. These same tactics are what is used in wire transfer fraud emails where attackers get employees to wire out tens of thousands of dollars from the company accounts to things like fake vendor accounts the attackers set up. The FBI refers to these as Business Email Compromise messages (BEC). The broader interpretation is any external email coming in, claiming to be from an internal user (like the CEO) wanting an employee to do something that compromises the integrity of business operations. This is a very dangerous attack vector because of how successful it is. With the damage companies face in the millions per year in losses.
What can you do?There's unfortunately no single fix to rule them all when it comes to blocking phishing in general. Attackers are constantly testing new methods and finding what works and what gets to the user's inbox. But there are some steps an organization can take to try to combat them.
Use encrypted email - Have it be company policy that certain bits of sensitive data should always be encrypted when sent via email. Ideally no information would ever be sent externally, but by following this protocol, the data would still ideally remain secured and unusable by the third-party. Look at the recipient address when replying - A quick glance to the "To": address when replying could potentially stop many of the spearphishing attacks. Attackers like to use things like freemail accounts (Outlook, Gmail, Yahoo, etc.) in the Reply To: field in a message in when phishing. This is only visible to most users once they go to reply. If they are willing to spend a few dollars, they even register domain names very similar to the victims domain. Have 2-factor verification - Having a company policy where it's acceptable to transfer $50k with a single email request is a bit loose with the coffers. It's best for everyone if there is a second verification in place such as a quick office visit or phone call. Same with sending around something like all employees W-2 files. Hover over links in messages - Sometimes spearphishing is aimed at just that single email communication to get through to a user and doesn't need the back and forth. Such as providing a phishing link looking for their email login, linking all the information to do a wire transfer for an external site, or even providing a link for the employee to upload sensitive company data to. Knowing where you are going online by hovering as well as glancing at URLs once you are there is a common security tactic that some people need to follow more closely. Don't be afraid of your boss - Yeah, this can be a tough one. But some of these spearphishing emails rely on using the CEO name as a strong-arm to get an employee to do something. By writing the text in a way that sounds urgent or demanding, some employees may forgo any set policy and bypass procedures in place to please their boss. After all, they think the CEO is ordering them to. Obviously questioning every order that comes down isn't feasible or advisable, but again there are certain things like sending W-2s and wire transfers that should have set policies in place where everyone follows them no matter what. It's better to question all wire transfers than to miss that one and send $20k to some foreign account. Use an email filter - This can be the obvious one here. But many email filters have some advanced features and tests that can catch these sorts of attacks that people may not be aware of. At AppRiver, we have an advanced spearphishing test that can look for these types of low-key phishing email tactics and stop them. If you have a filter service that doesn't have spearphishing features in it, you can even do something like block external email using your domain name in it, so that any email using your domain name, but coming from somewhere that's not your own server, gets blocked. Or enable SPF on your own domain and verify that on any incoming messages.