Locky Ransomware Going Strong
Blog
Thought Leadership
Locky Ransomware Going Strong
Troy Gill

 It’s no secret that ransomware has been circulating at a fever pitch on the web as of late. Locky remains the most prolific despite the fact that new variants of ransomware being discovered with greater regularity. This morning we have been monitoring a campaign attempting to distribute Locky to millions of unsuspecting users. We have already quarantined over 3 million emails this morning associated with several different variations attempting to spread Locky. Lately, they seem to have taken a “less is more” approach to their attacks. Most messages have very little aside from some generic phrases along with an attachment, in this case a macro-enabled document. These are also being spoofed to appear to have come from a user at the same domain as the recipient and are posing as a scanned document.
It’s no secret that ransomware has been circulating at a fever pitch on the web as of late. Locky remains the most prolific despite the fact that new variants of ransomware being discovered with greater regularity. This morning we have been monitoring a campaign attempting to distribute Locky to millions of unsuspecting users. We have already quarantined over 3 million emails this morning associated with several different variations attempting to spread Locky. Lately, they seem to have taken a “less is more” approach to their attacks. Most messages have very little aside from some generic phrases along with an attachment, in this case a macro-enabled document. These are also being spoofed to appear to have come from a user at the same domain as the recipient and are posing as a scanned document.
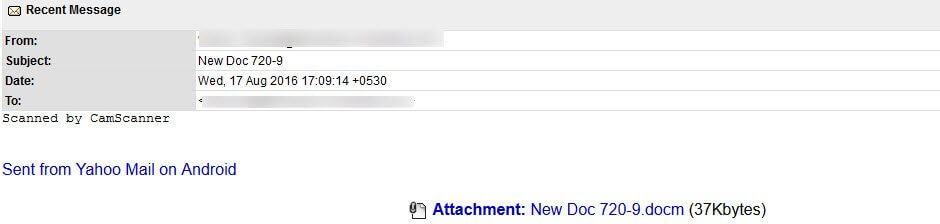
The following is an example of this morning’s traffic:
Once infected, all of the users files are encrypted. This is followed shortly after by a prompt to pay the ransom. Though some current ransomware variants have corresponding tools online to help the victims decrypt their files, none seem to be a viable solution to this threat. A good backup strategy can save you from having to pay the ransom in these attacks. However, we have seen some recent ransomware variants such as CryptXXX that are also stealing the sensitive data in addition to encrypting and this is a trend that we expect to see continue in the future.
Here are a few steps you can take to limit the potential impact of ransomware
Maintain several robust layers of prevention Consider banning macro-enabled files throughout your organization No matter how innocuous a message may seem, never open an attachment in an unsolicited email --regular user training to improve Keep regular hot and cold backups