Adobe Phishing links in PDF
Blog
Thought Leadership
Adobe Phishing links in PDF
Jonathan French
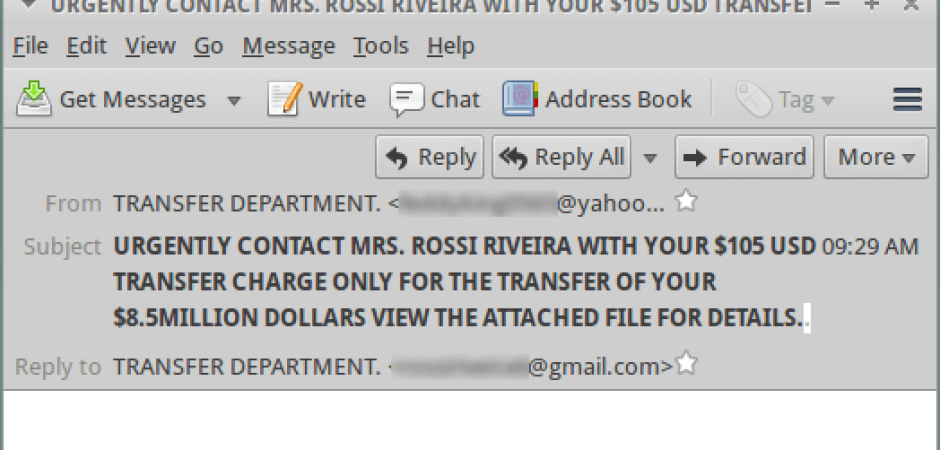
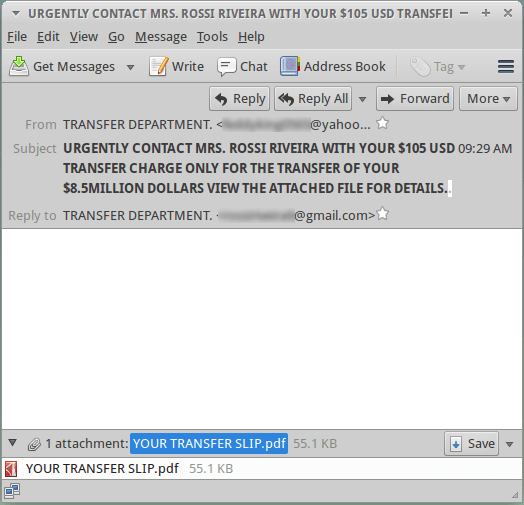
We noticed a phishing campaign this morning that used some interesting redirects we don't see too often. The email itself was plain and the body empty, with the only thing standing out being the very long subject line. The long subject line, empty body, and from/reply-to info should set off some red flags for most people.
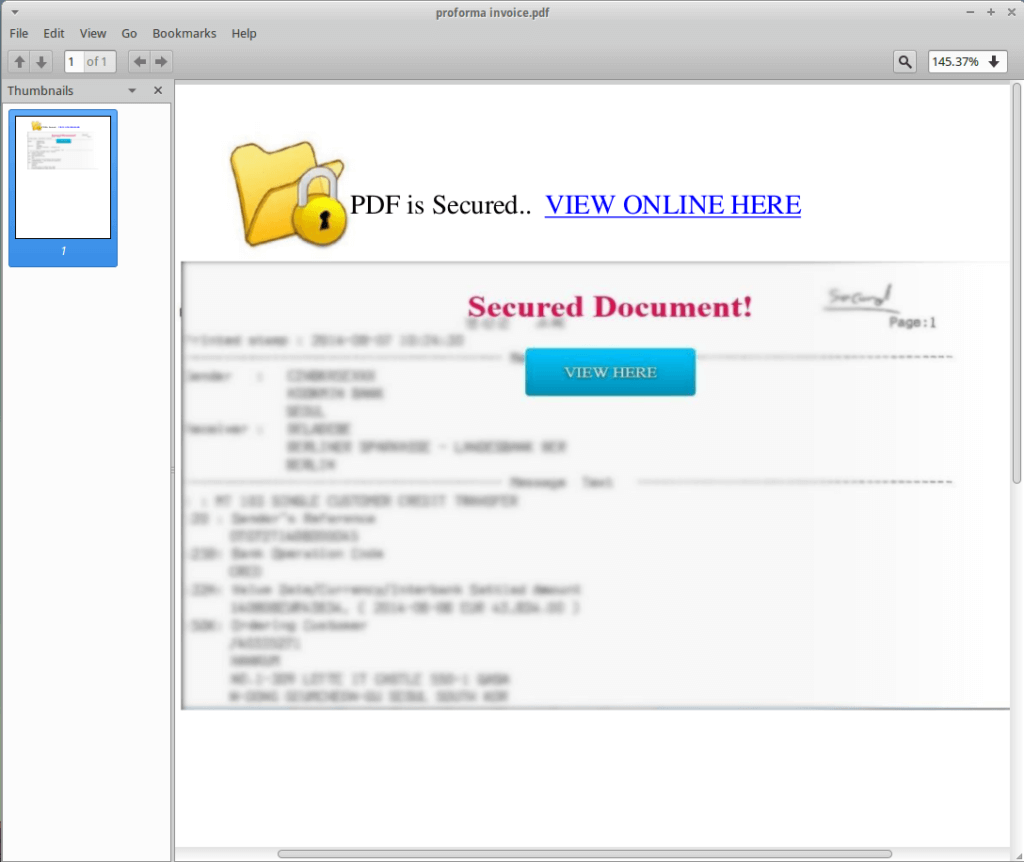
Opening the PDF you are presented with a pretty standard layout for a lot of phishing methods. With the background blurred and a note saying you need to perform these steps to see the file, some users may have their curiosity get the better of them and be more likely to click and see what they're missing out on. This is used a lot in phishing, but even more so in things like Macro Malware. We're written a few times on the topic and one of the common tactics for the malware authors is to always try and trick a user to clicking enable content on a macro file to run the malware.
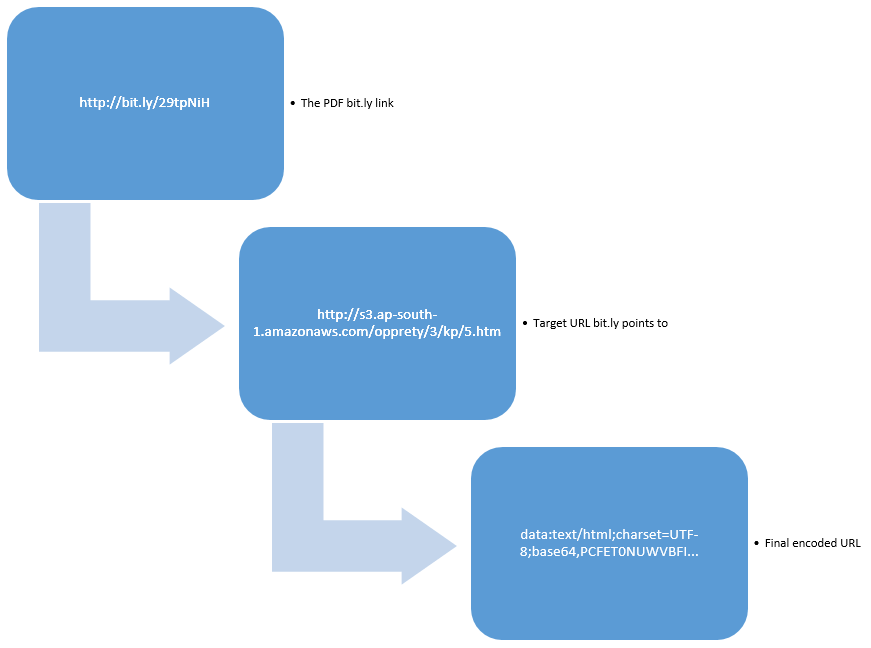
Next is where the redirects happened. The breakdown is that the link embedded in the PDF is a bit.ly link ( a very popular url shortener service), that bit.ly link redirects to an Amazon AWS hosted site. The Amazon site returns some javascript with another URL redirection, but this time it uses the URL field itself to store the data. This is a feature that not many people seem to know about, where all the content you see is stored in the URL and base64 encoded.
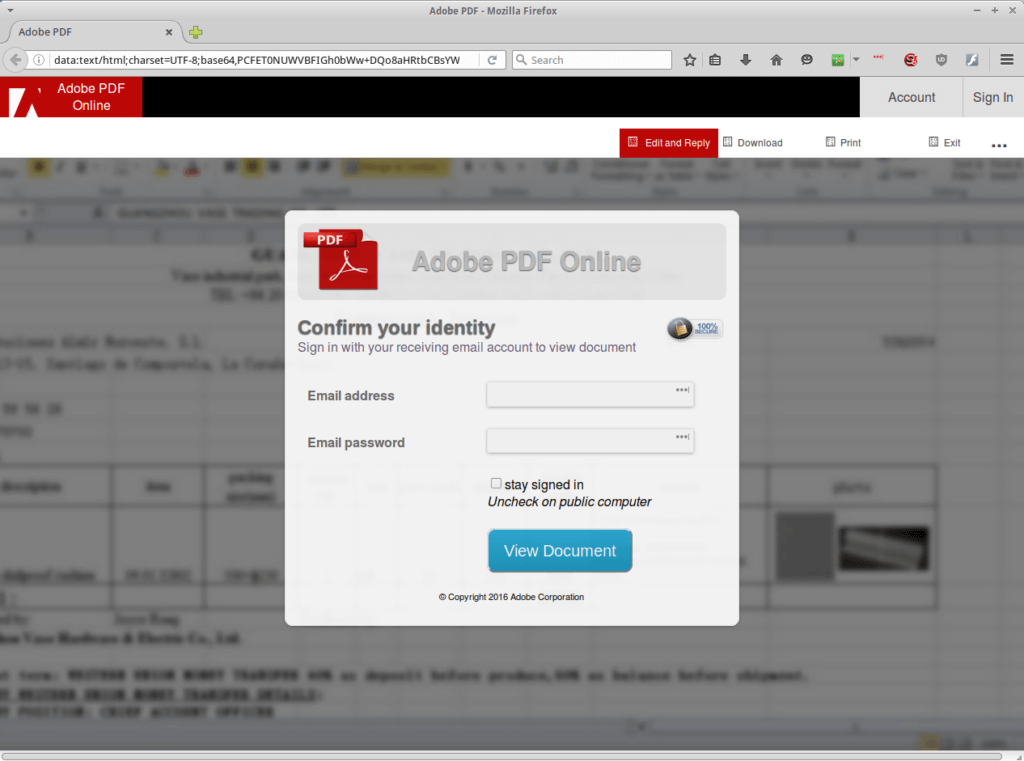
The final page is the familiar phishing page that is expected. Entering in credentials in to this page will make a POST to a remote server at colloquedadie-ci.org, then redirect you to a blank PDF file at geocities.ws
Many times we see these sorts of redirect tactics used in attempts to bypass systems that look for phishing links. Misdirection is a constant and evolving tactic for spammers and malware authors as they can often vary a campaign enough to try and bypass filtering. While many phishing campaigns can be small or targeted, they can still have a large impact on the victims. Unfortunately if users aren't aware of what to look out for, they can not only fall victim to these types of scams, but also not realize they are the victim. Just shrugging off a weird message like this and not immediately resetting your password could give an attacker enough time to start gaining access to accounts you provided or do research and see where else you may have an account online (just searching for a users email address will often show other sites it is associated with). With the large amount of people reusing passwords, they can possibly get access to even more of the accounts than the one the user provided originally. And with access to your email account, they could simply send password reset emails to it and reset your passwords. So it's important to always be vigilant with any unfamiliar emails you receive. So always check what website you are actually at and look before you click links. Even if a web page looks convincing, a quick glance at the address bar could save you from falling victim to phishing links.