TeslaCrypt Continues Its Tirade
Blog
Thought Leadership
TeslaCrypt Continues Its Tirade
Fred Touchette
This morning we are continuing to see attacks from one of the major contenders in the Ransomware game, TeslaCrypt. TeslaCrypt began its career back in February of 2015, fresh on the heels of another popular piece of Ransonmware known as CryptoLocker. Most often delivered via the Angler Exploit Toolkit, we most often see Tesla infecting websites to deliver drive-by downloads to those unlucky enough to stumble upon these websites. Recently, however, new versions of this malware have begun to be use botnet delivered email as a means of delivering its payload to its victims.
In its inception, TeslaCrypt targeted gamers by not only encrypting photos and documents, but also targeting saved game files and Steam activation keys. Since then this family of malware has moved on to corporate targets and now on to whomever it can find.
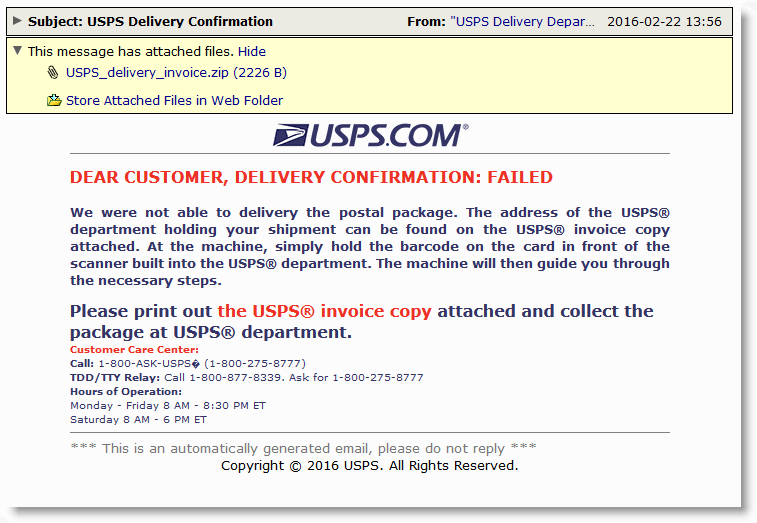
Today's samples are varied but mostly surround a campaign designed to look as if it it was delivered by the United States Postal Service. The emails utilized colors and graphics to add to the stratagem. These emails offer an attachment to its victims which is supposed to be the invoice receipt of a failed delivery attempt. This file is a zipped archive that contains a simple short obfuscated javascript file that acts as the downloader. In this particular ploy, the filenames used are USPS_delivery_invoice[.]zip for the archive and within, the javascript files use the following naming convention - invoice_[random string] .js, invoice_copy_[random string] .js, or invoice_scan_[random string] .js.
Once executed the javascript downloader reaches out to one of several websites including: mafiawantsyouqq[.]com, lenovowantsyouff[.]com, whereareyoumyfriendff[.]com, lenovomaybenotqq[.]com, and ikstrade.co[.]kr to pull down files such as 93[.]exe, 45[.]exe, and 26[.exe] among others utilizing the same naming convention. Some versions also reach out to make an http post command to salaeigroup[.]com.
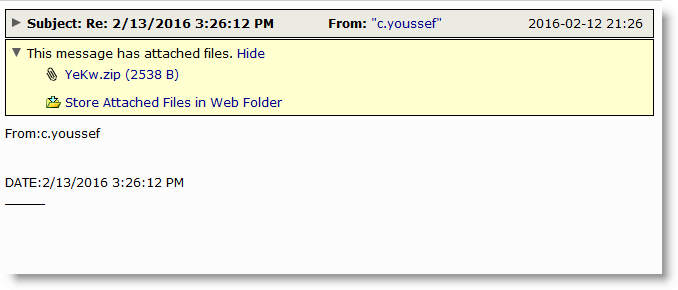
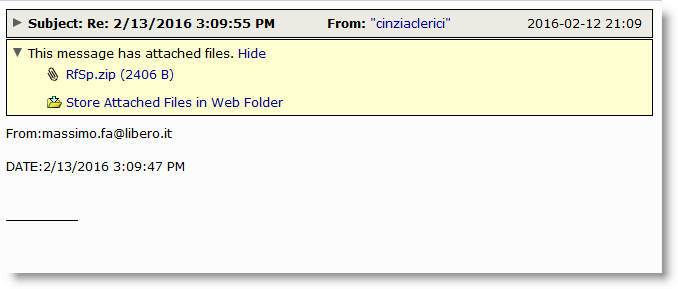
In addition to this USPS themed attack, we are simultaneously seeing these very same javascript files attached to emails that are much more plain in appearance and vague in content. These use a subject line that is simply a date and time format and a random 4 letter file naming technique as can be seen below. Another interesting fact about these versions is that some show an earlier received date even though they are coming in currently. This could either be by design or some of these could have been held up on their respective remote hosts until today, regardless, they remain just as dangerous and should be avoided.
AppRiver does have you covered for these attacks, but remain aware and vigilant as these Ransomware attacks show no real sign of slowing down, in fact they seem to be highly effective. In order to protect yourselves and to send a message to the attackers, it is imperative that users are aware that these are out there in full force, systems should be backed up often, and these ransoms should not be paid, nor will they have to be if you have followed this advice and have a proper backup strategy in place. Also, backup your files. Did I mention, you should probably perform regular backups? Do it! Backups.