Malicious Macros in Fake Adobe Messages
Blog
Thought Leadership
Malicious Macros in Fake Adobe Messages
Troy Gill
Over the past six months we have seen an increase in the number of emails with malicious Word (.doc) attachments. These messages utilize the available functionality in a file type that is very familiar to basically every computer user. By using this technique the attacker can increase the chances that one of these messages will be opened.
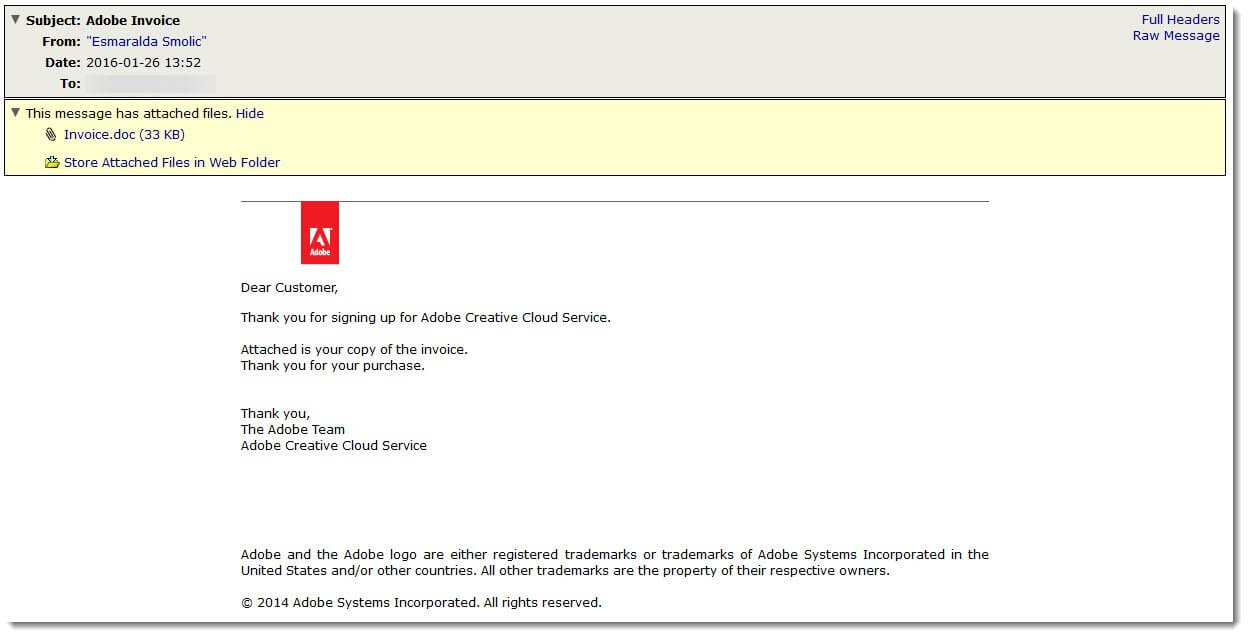
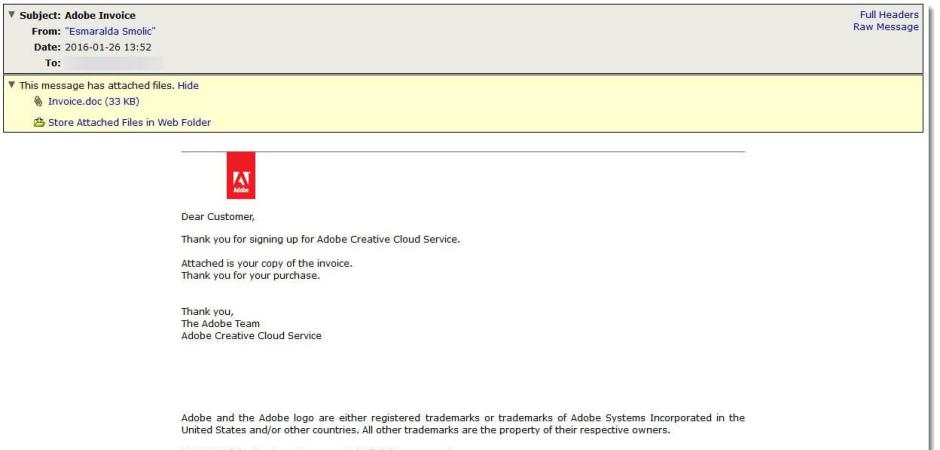
An interesting variant of the macro malware that we have been seeing hit our filters over the past few days is posing as an invoice from the also highly recognizable Adobe. The messages are quite simple in nature, thanking the recipient for their “purchase” of Adobe Creative Cloud Service. The messages all contain an attachment Invoice[dot]doc (MD5: 6767089af607eb6464374bb89ead8e3e).
Once the document is opened all the user has to do is click enable editing/content and the macro will infect the machine.
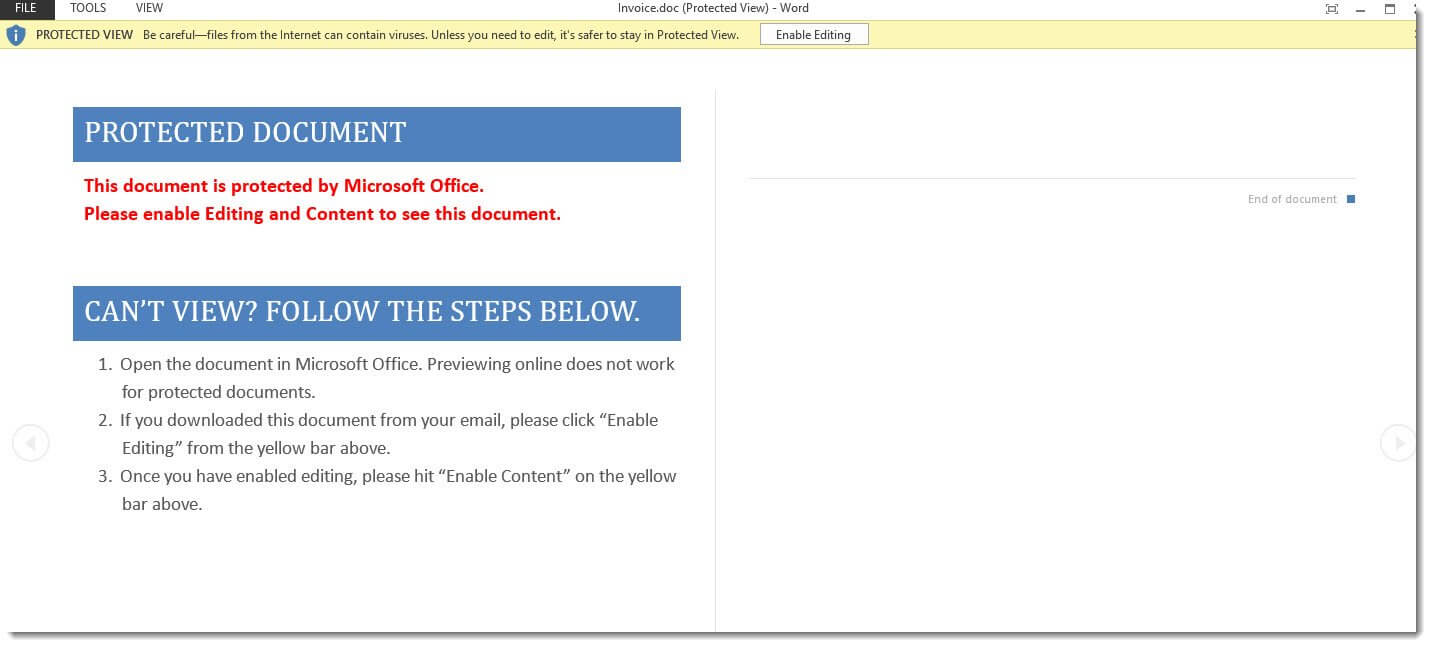 This particular instance installs a fairly generic Trojan Downloader commonly referred to as some variation of “Downloader.VBA.Agent”.
This particular instance installs a fairly generic Trojan Downloader commonly referred to as some variation of “Downloader.VBA.Agent”.
Of course our customers are protected from all variants of this threat. However, if admins want to take it a step further they should consider disabling macros entirely using group policy if possible--that way they can combat documents with malicious macros that might make their way onto the network from any vector.