Amazon themed malware targets Crypto Currency
Blog
Thought Leadership
Amazon themed malware targets Crypto Currency
Troy Gill
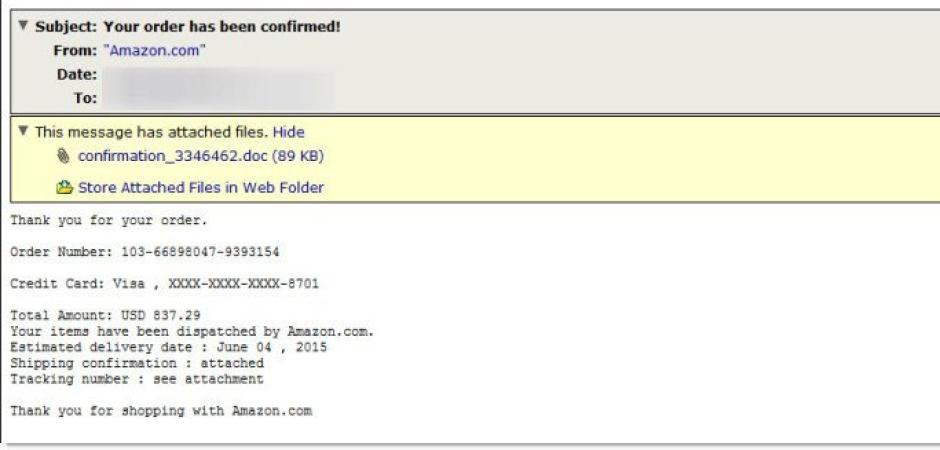
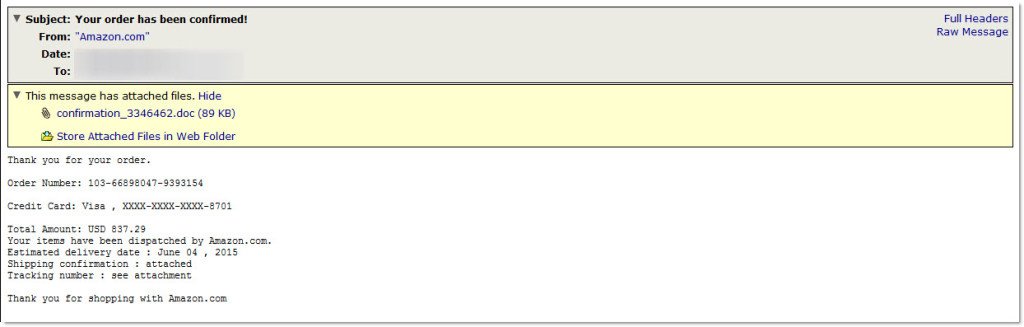
Over the past week we have been monitoring (and blocking) a stream of malicious emails attempting to pose as legitimate Amazon purchase confirmations. The messages simply state that your order has been confirmed and contains a small amount of details. The user being target is directed to the attached .doc file for the shipping and tracking details.
In order for the .doc (MD5sum=998692c0e93d4821c069aa96ddff800c) to actually infect the user’s machine they must have Macro’s enabled for MS Word. Thankfully for most users, Macros are disabled by default in current versions. However, for those who already have it enabled or chose to follow the prompt and enable them an infection will occur. The malware contained in these messages is identified as part of the Fareit malware family. This family of malware is often distributed via Word documents with malicious macros embedded and has been known to drop multiple malware variants on the target machine.
In this particular case the malware quickly goes to work attempting to steal your Outlook password along with website passwords from various browsers such as Firefox, IE, Chrome and Opera. It then attempts to harvest account credentials for a lengthy list of FTP and multiple file storage programs. In addition it begins pilfering the target machine for just about every type of Crypto currency in existence. Including:
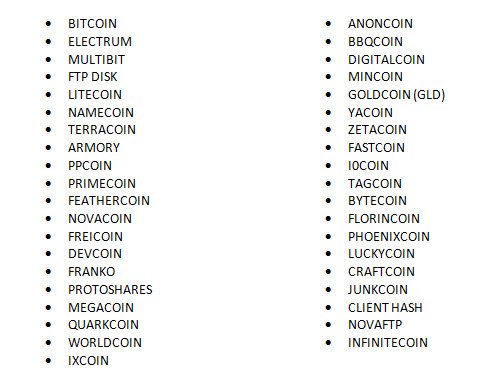 This behavior (stealing Crypto currency) is something we have been seeing with more frequency as of late. The anonymous nature and lack of regulation in the Crypto Currency market make it more akin to stealing actual cash than to committing wire fraud by raiding someones online bank accounts. But in this case the cybercriminals are o.k. with that too… The last observed behavior was to drop a copy of the Zeus Trojan to be used to capture and steal bank related information.
This behavior (stealing Crypto currency) is something we have been seeing with more frequency as of late. The anonymous nature and lack of regulation in the Crypto Currency market make it more akin to stealing actual cash than to committing wire fraud by raiding someones online bank accounts. But in this case the cybercriminals are o.k. with that too… The last observed behavior was to drop a copy of the Zeus Trojan to be used to capture and steal bank related information.