Cryptowall Coming in SVG Files
Blog
Thought Leadership
Cryptowall Coming in SVG Files
Jonathan French
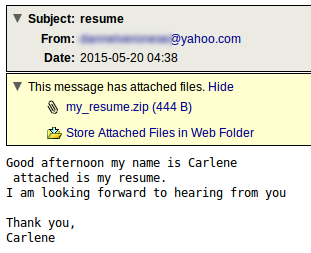
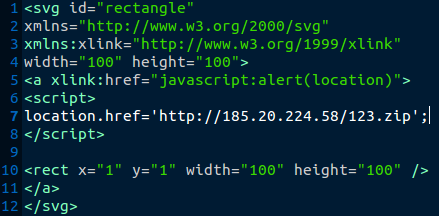
This morning we had a malware campaign with zipped svg files attached in the messages. SVG files are normally used for images and supports some interactive features. An example would be maybe something like a graph on a webpage that showed some info when hovering over an option. These SVG files however contained a small javascript entry that would open a webpage to download some malware.
The IP link in question ends up forwarding to another domain where a zip is downloaded of the actual exe payload. It didn't auto execute, user interaction would still be needed for that. The payload this time around is Cryptowall. When the file executes it creates HELP_DECRYPT.TXT, HELP_DECRYPT.PNG, HELP_DECRYPT.HTML, and HELP_DECRYPT.URL files that have all been associated with Cryptowall infections. Searching any of those file names online brings many write ups on the virus family. It also created a public RSA key and entered it in to the registry (the key used with encrypting the files). After giving it just a few minutes, indeed the popup about Cryptowall 3.0 popped up with steps to pay. Crypto ransomware has proven many times it is effective for attackers in getting users to actually pay the ransom. The tactic is still alive and likely to continue evolving. With the attacks still being prevalent, it's a good idea to make sure you are covered with data backups that cannot be potentially accessed by the malware (it's been known to encrypt network shares and NAS units).
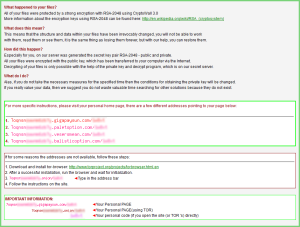 The original notification pop up on the PC
The original notification pop up on the PC
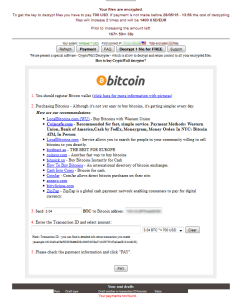 The website on Tor showing how to pay the $700 to decrypt files.
The website on Tor showing how to pay the $700 to decrypt files.
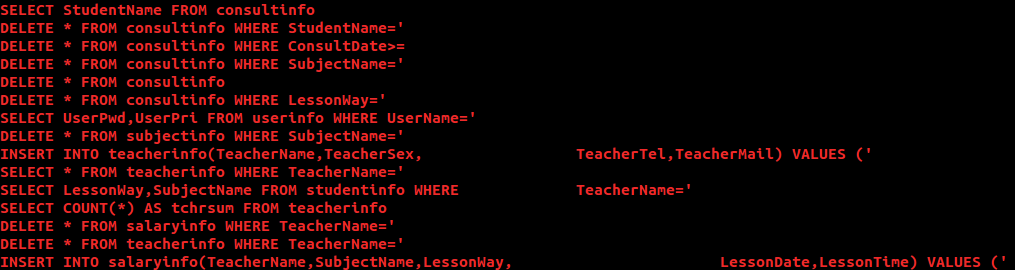
And the interesting bit of info I noticed while looking at the exe that was downloaded, was that it had sql commands hard coded in it. Looking closer they all seemed related to a potential schools sql database. Some of the recipients we stopped this malware for were schools but nothing seemed out of the ordinary with the volume of recipients, which was low volume in general. While it's possible the malware had other intentions from encrypting in mind, like to wreak havoc in a sql database, this was from a strings output so it was all plain text and the table naming conventions just seem a little too plain as well. However, someone knowing sql table names or a school using a plain naming convention could be problematic if the malware were to attempt to attain access and do its thing. It's certainly also a tactic for malware authors to add in code that isn't used or code that fluffs up functions to distract from analysis and make analyzing more complex and time consuming. So that's a possibility. While these appeared to be part of valid functions, it looks like they were not used during testing. Though it's possible there were very specific parameters that needed to be met for this to go active and attempt sql changes.
Also, there was some ASCII art in the strings output. I had originally posted this upside down but after flipping it, it appears to be an animal holding a heart.