eHax
Blog
Thought Leadership
eHax
Fred Touchette
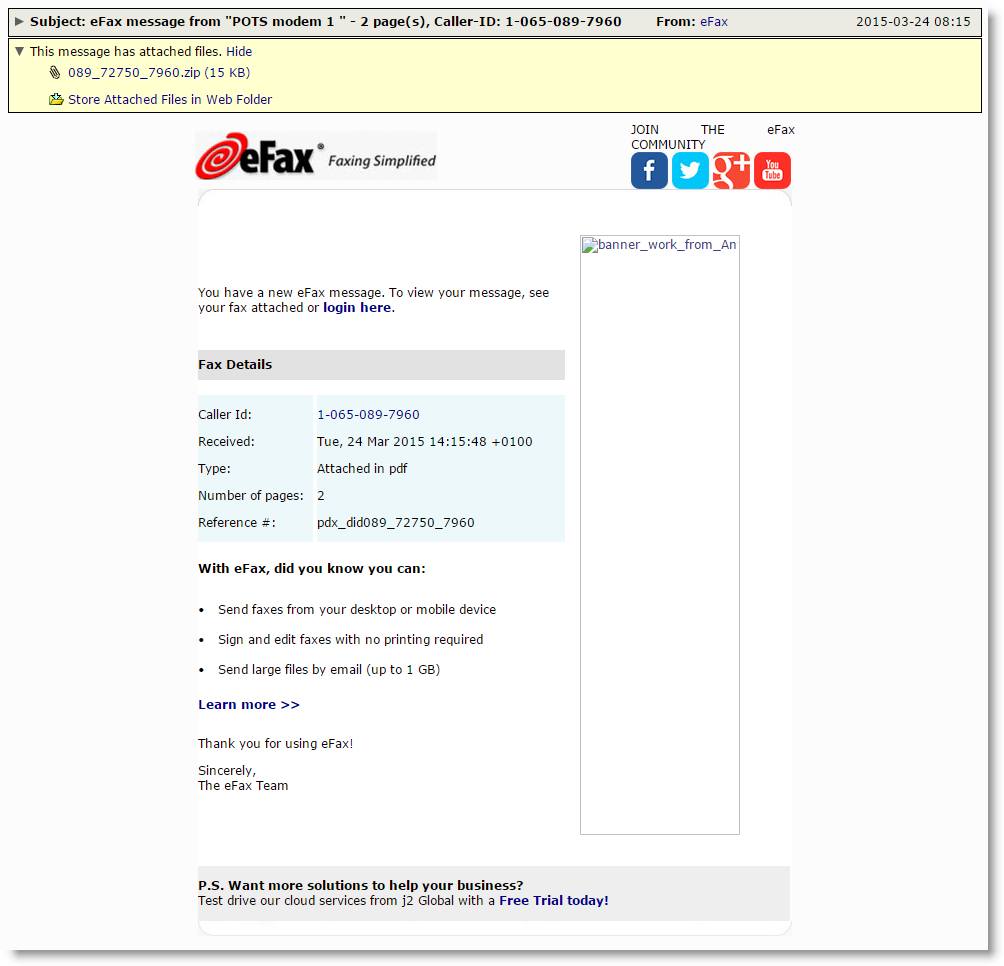
Over the past hour we've begun seeing a malware campaign hitting our filters that utilizes a common, and apparent favorite theme of the malware authors. These emails appear to resemble notifications from the eFax service that tons of people rely on to simplify their faxing needs. As is the case with a lot of these, actual logos and templates from real eFax notifications are used to trick the recipient into believing that these are just another ordinary eFax email and not a malicious facsimile (see what I did there?). However there are a couple of red flags that people should have noticed. One of the biggest is the fact that one of the banner graphics in the email is broken. The table is pointing towards an actual eFax file location, but it doesn't appear to be there, possibly removed in order to be replaced by a newer advertisement. Another clue would be the supposed phone number presented in these emails. These are all randomly generated to look like real phone numbers as well as making every email just a little bit different in order to make blocking them a little more difficult as well. However, because they are randomly generated, some of them don't exactly resemble phone numbers, such as the example below where the area code as well as the telephone prefix begin with the number zero, which you will not see in the United States.
Another huge clue is that the attachment arrives as a zip file which you likely won't see coming from eFax, also inside that Zip is an executable (which you really won't see) named IMG.exe, they did try to disguise it by giving it a Pdf icon, although the icon itself is oddly pixelated, which I've seen more than once in different malware campaigns. I can't be exactly sure what the point is in this or if it just occurred due to automation errors, that remains to be seen. It does serve as a sort of calling card though that more than likely links the origin of the campaigns that share this trait.
If someone was unlucky enough to receive one of these and ran the executable, they wouldn't notice very much going on on the surface, but behind the scenes the malware begins by making copies of itself and deleting the original executable in order to hide itself in the newly infected system. The sample then makes various checks for network connectivity before proceeding to receive instructions from command and control. We have seen nearly 300,000 pieces from this run so far, and at the time of capture, only 4 out of 57 AV's recognized this piece of malware according to Virustotal, but AppRiver clients were safe as we proactively had protection in place to protect your inboxes.